GitHub - gibsjose/bcrypt-hash: Generate secure cryptographic hashes from the command-line using `bcrypt`

Password security of encrypted SSH private key: How to read round number or costfactor of bcrypt - Server Fault
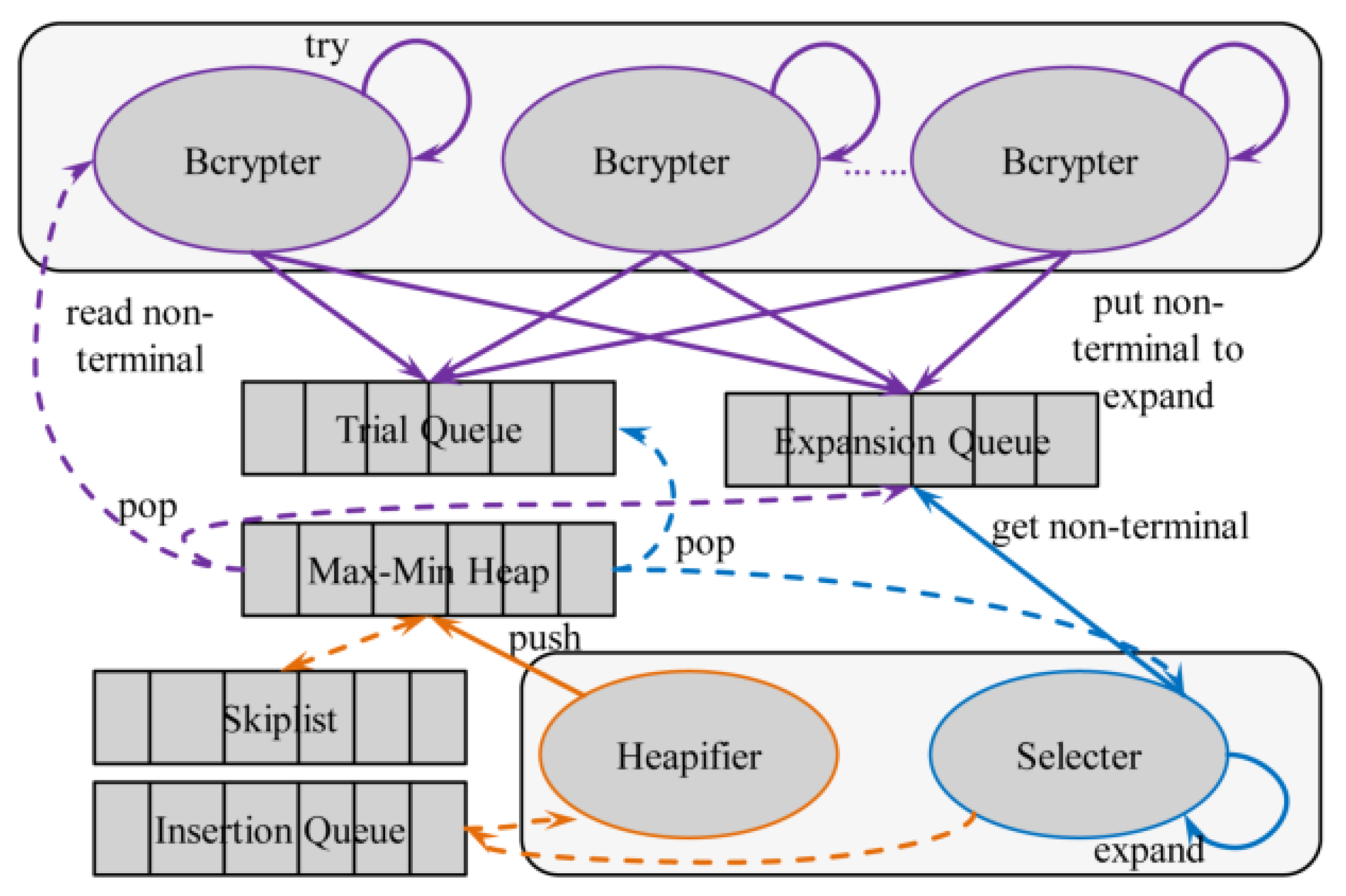
Symmetry | Free Full-Text | Study on Massive-Scale Slow-Hash Recovery Using Unified Probabilistic Context-Free Grammar and Symmetrical Collaborative Prioritization with Parallel Machines