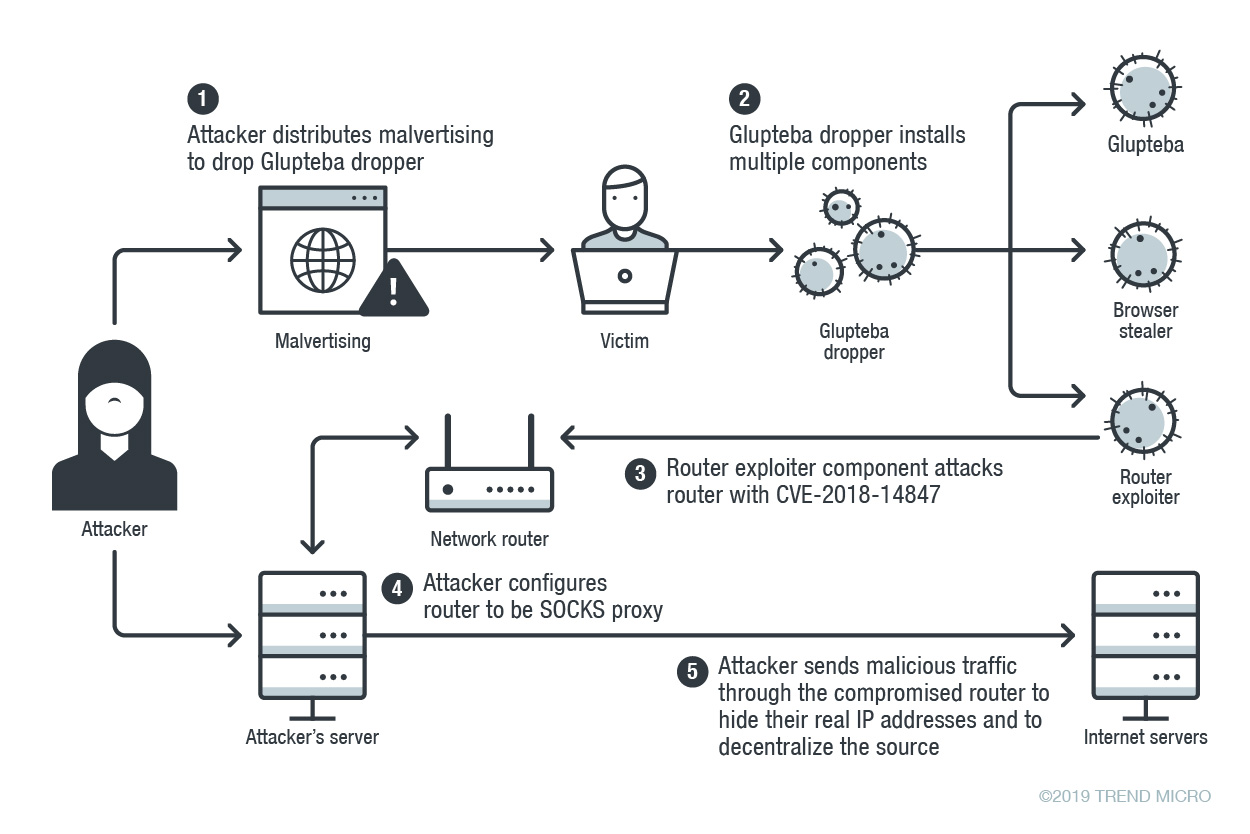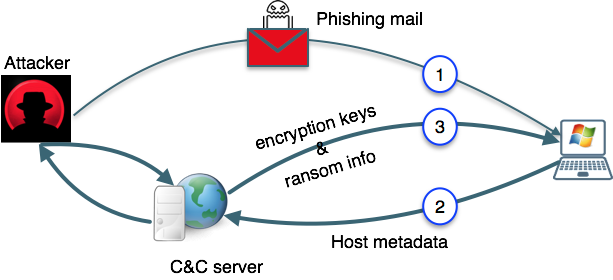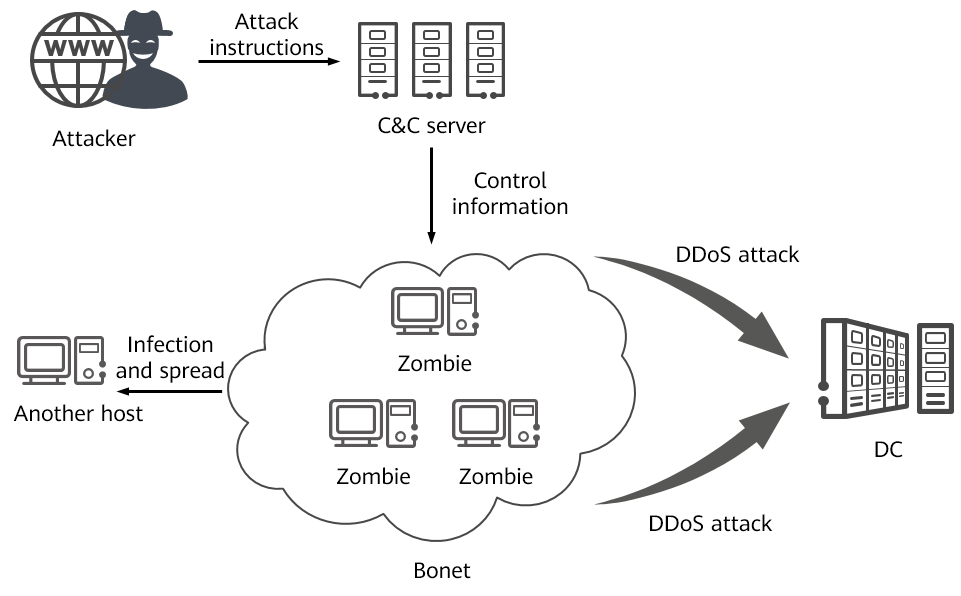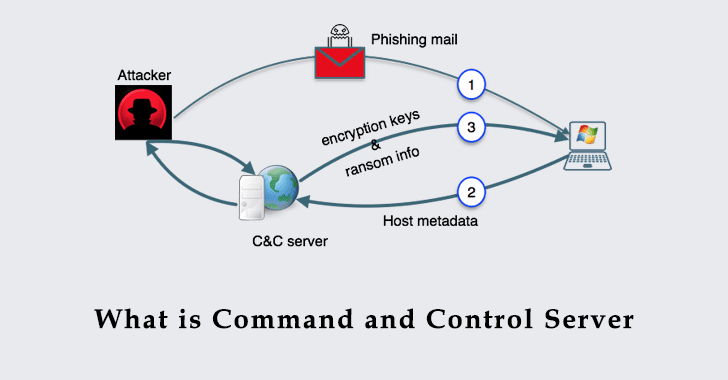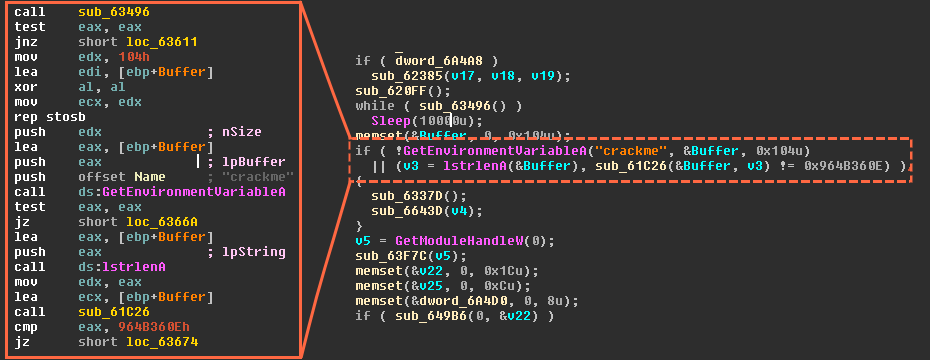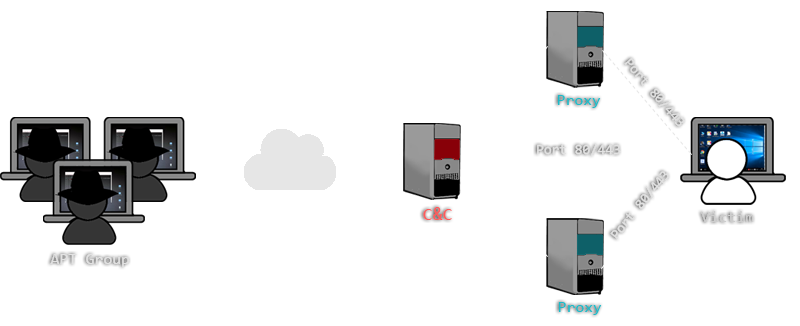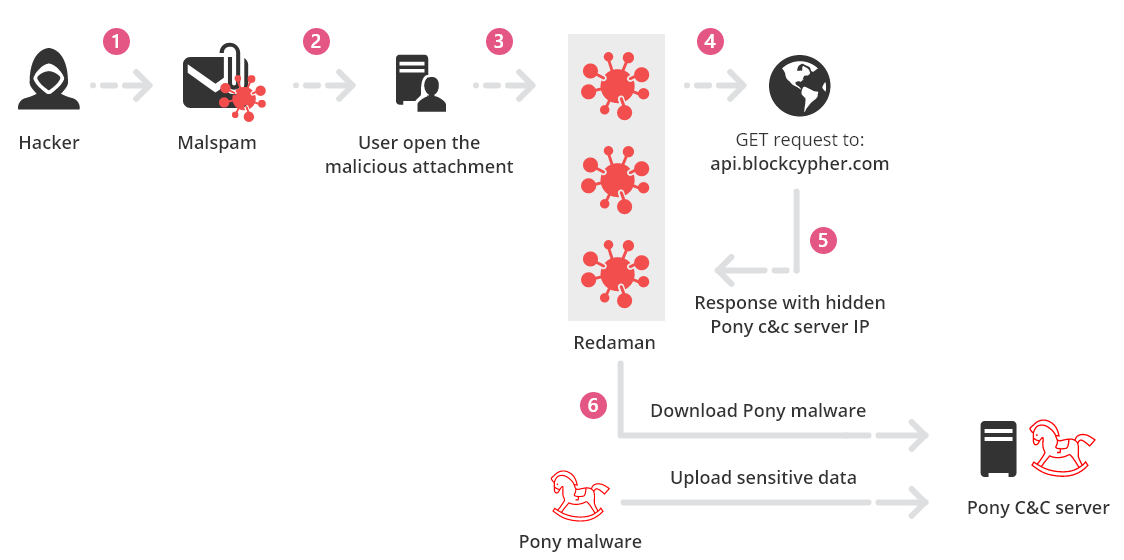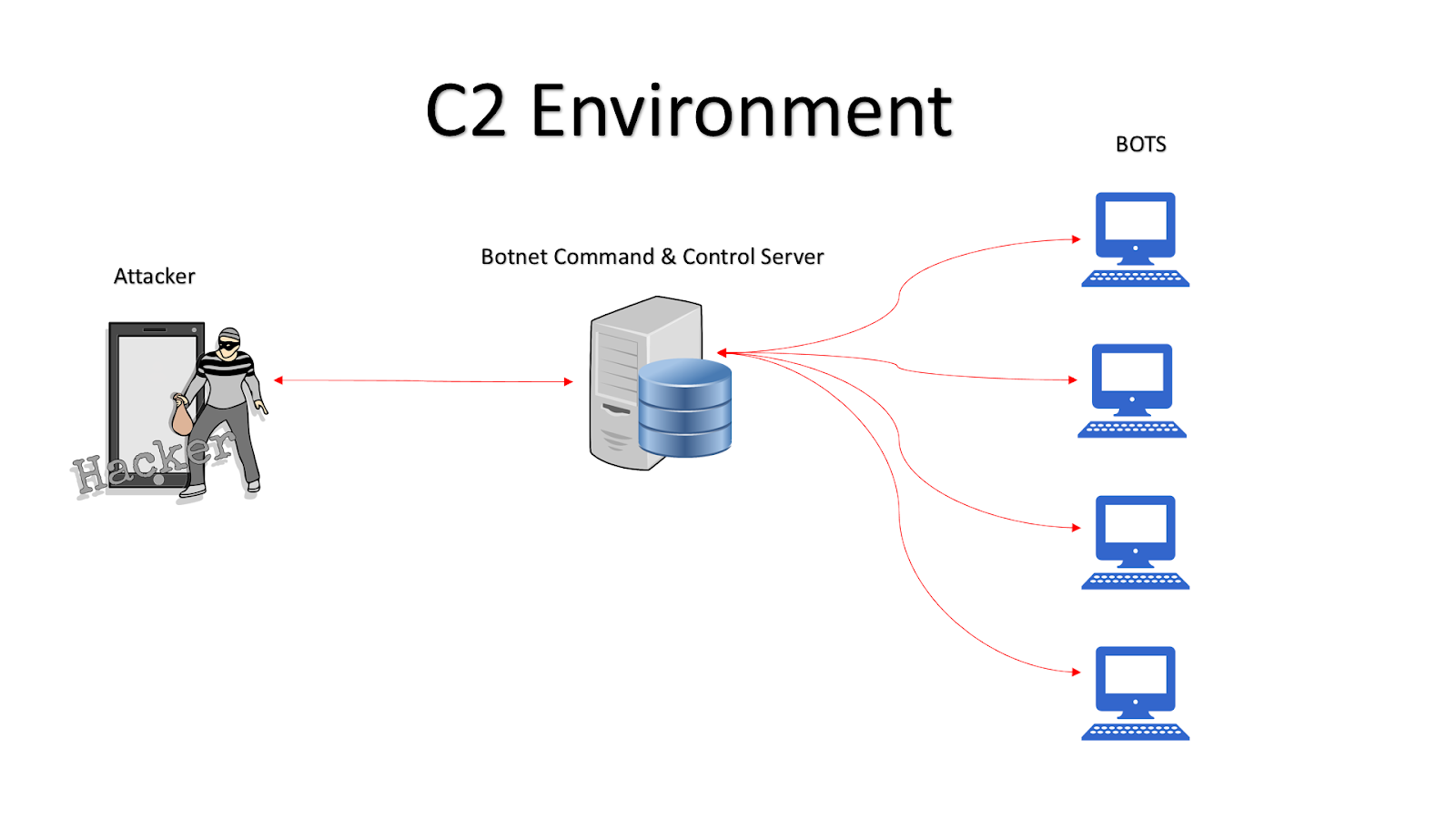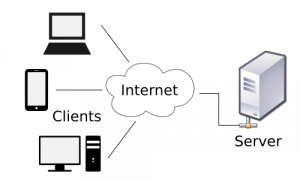
Basic Understanding of Command and Control Malware Server - Penetration Testing and CyberSecurity Solution - SecureLayer7

Obtain C&C Channel. Command and Control is a key role to… | by Mohans | Redteam & Blueteam Series | Medium

Malware hides C&C server communications using Google Docs function - Security AffairsSecurity Affairs

New Miori Malware Uses Text-based Protocol to Communicate with C&C Server for Launching a DDoS Attack | CyberCureME
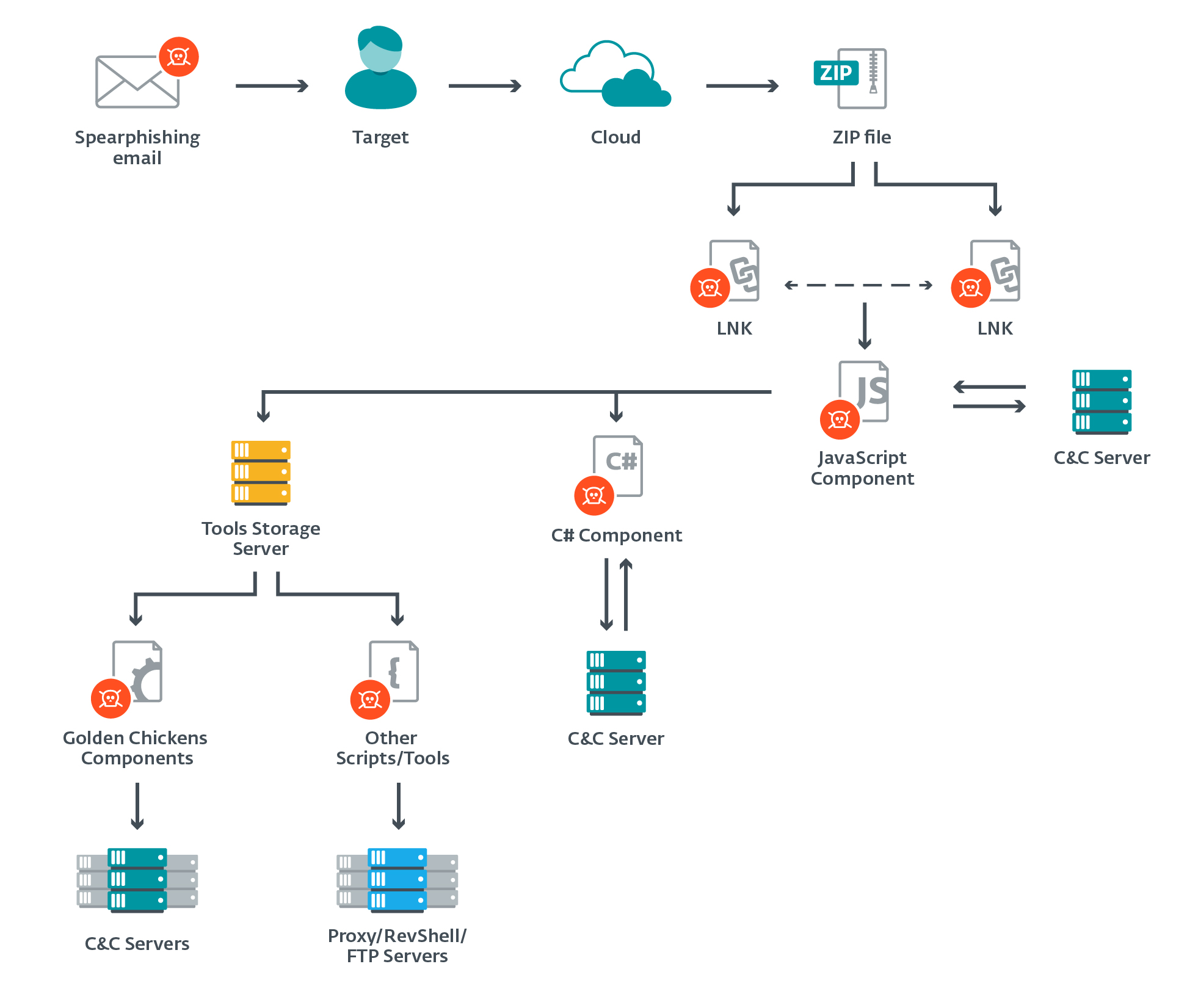
Ο χρήστης ESET research στο Twitter: "#Evilnum uses several malicious components in its attacks. Each operates independently and has its own dedicated C&C server. The JS backdoor initially compromises the system and