
Cyber Security and Threats: Concepts, Methodologies, Tools, and Applications (3 Volumes): 9781522556343: Security & Forensics Books | IGI Global
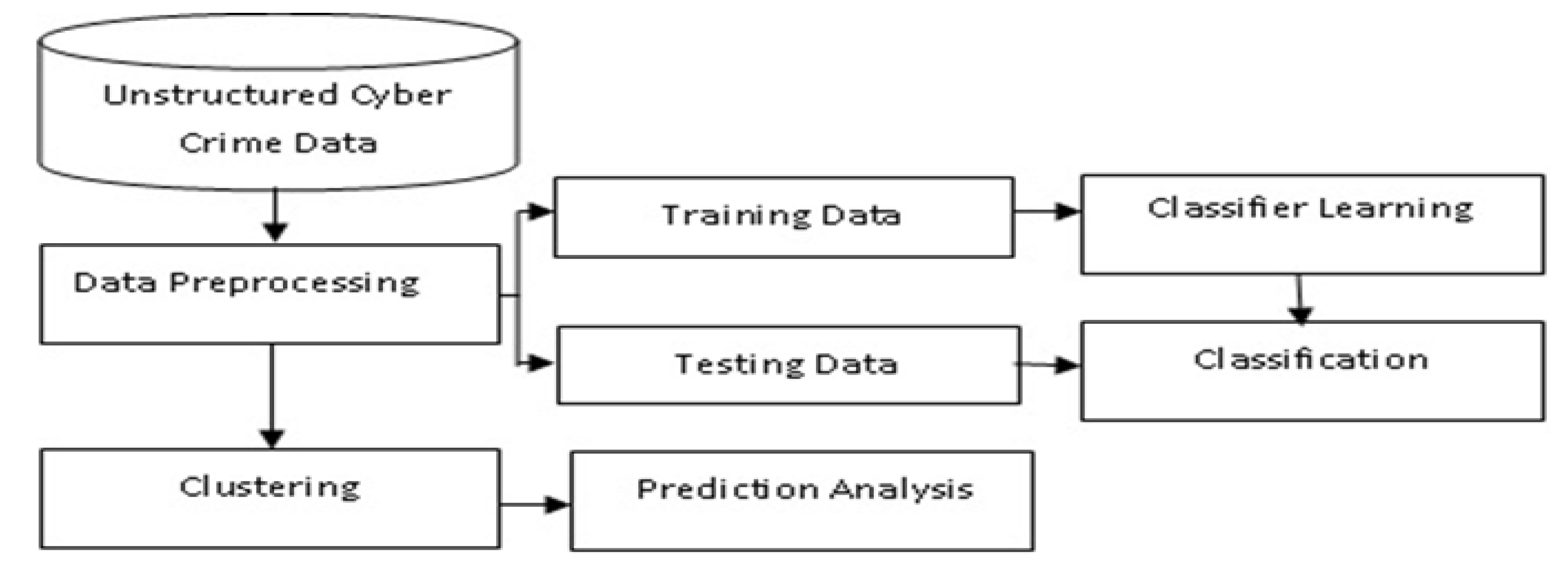
Sustainability | Free Full-Text | Computational System to Classify Cyber Crime Offenses using Machine Learning | HTML

Cyber Law, Privacy, and Security: Concepts, Methodologies, Tools, and Applications (3 Volumes): 9781522588979: Security & Forensics Books | IGI Global
Evaluating Criminal Transactional Methods in Cyberspace as Understood in an International Context · CrimRxiv

Cyber Crime: Concepts, Methodologies, Tools and Applications: USA Information Resources Management Association, USA Information Resources Management Association: 9781613503232: Amazon.com: Books

Cyber Crime: Concepts, Methodologies, Tools and Applications: USA Information Resources Management Association, USA Information Resources Management Association: 9781613503232: Amazon.com: Books






![Cybersecurity Best Practices for 2022 [15 Data Protection Methods] | Ekran System Cybersecurity Best Practices for 2022 [15 Data Protection Methods] | Ekran System](https://www.ekransystem.com/sites/default/files/15%20best%20cybersecurity%20practices/open-15-graph-Cybersecurity-Best-Practices-to-Prevent-Cyber-Attacks-in-2022.jpg)




