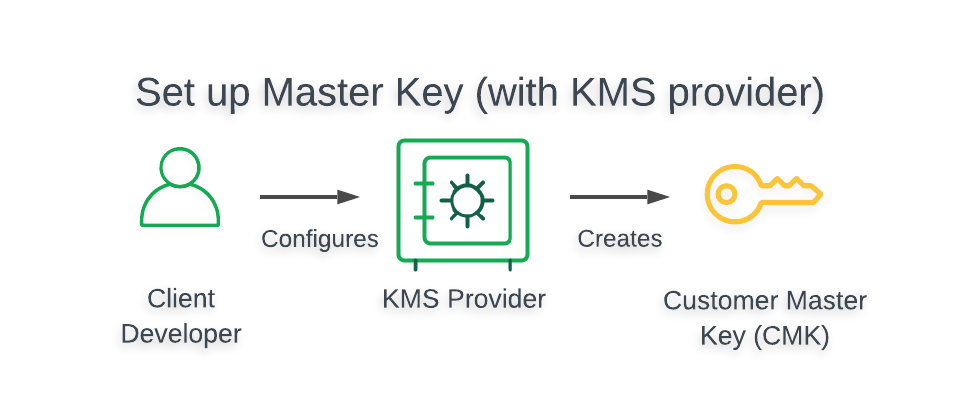
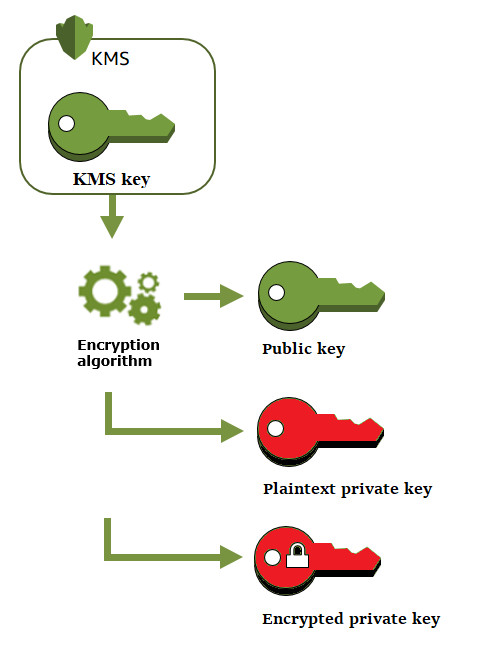
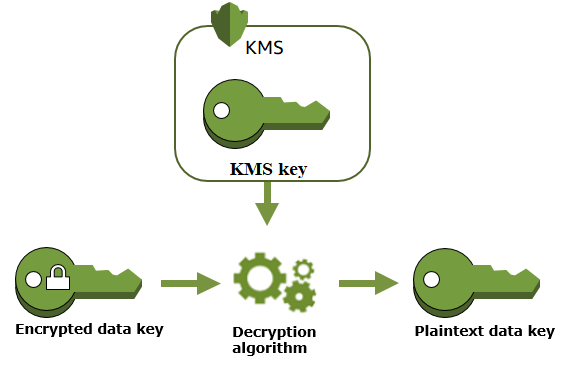
100 Days of DevOps — Day 22-Introduction to Key Management System(KMS) | by Prashant Lakhera | Medium
Amazon Web Services (AWS) Key Management Service (KMS) Encryption Plugin Setup Guide - MariaDB Knowledge Base
![Server-side encryption with KMS managed keys (SSE-KMS) - AWS Certified Solutions Architect - Associate Guide [Book] Server-side encryption with KMS managed keys (SSE-KMS) - AWS Certified Solutions Architect - Associate Guide [Book]](https://www.oreilly.com/api/v2/epubs/9781789130669/files/assets/0faf29ee-4a0b-4a29-99f5-c4e1ec042047.png)
Server-side encryption with KMS managed keys (SSE-KMS) - AWS Certified Solutions Architect - Associate Guide [Book]