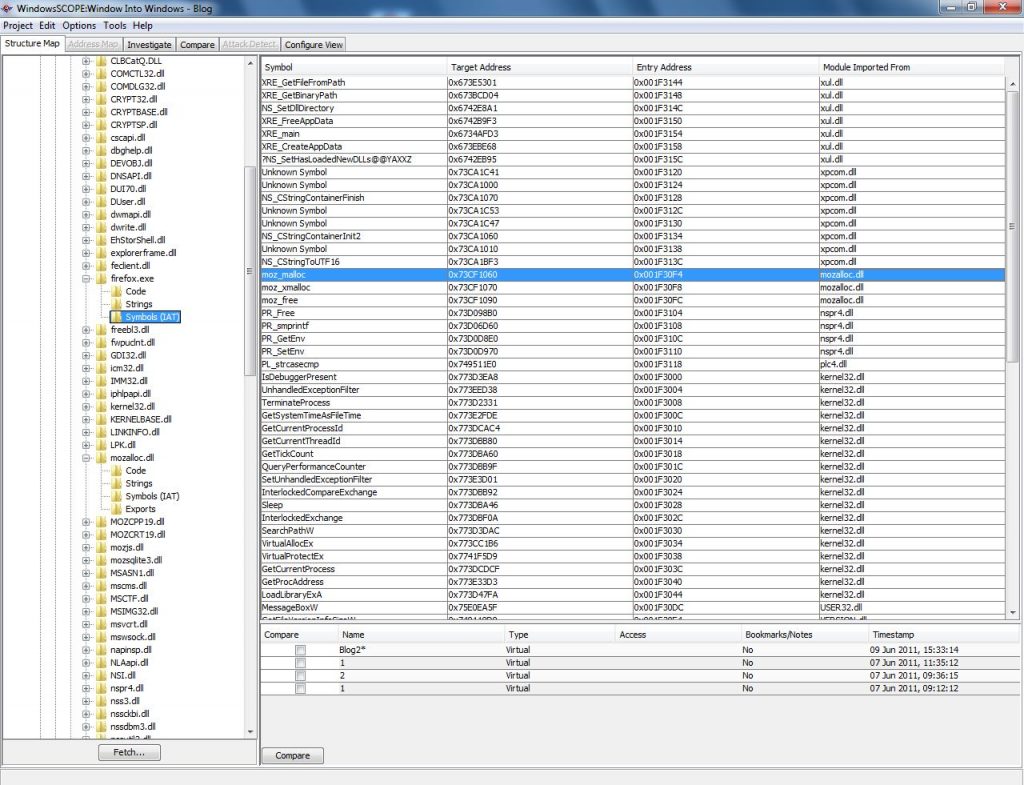
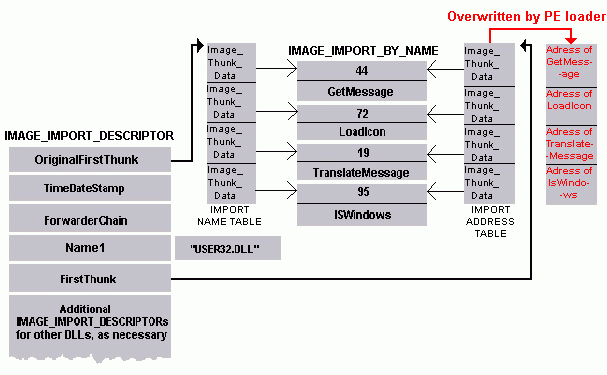
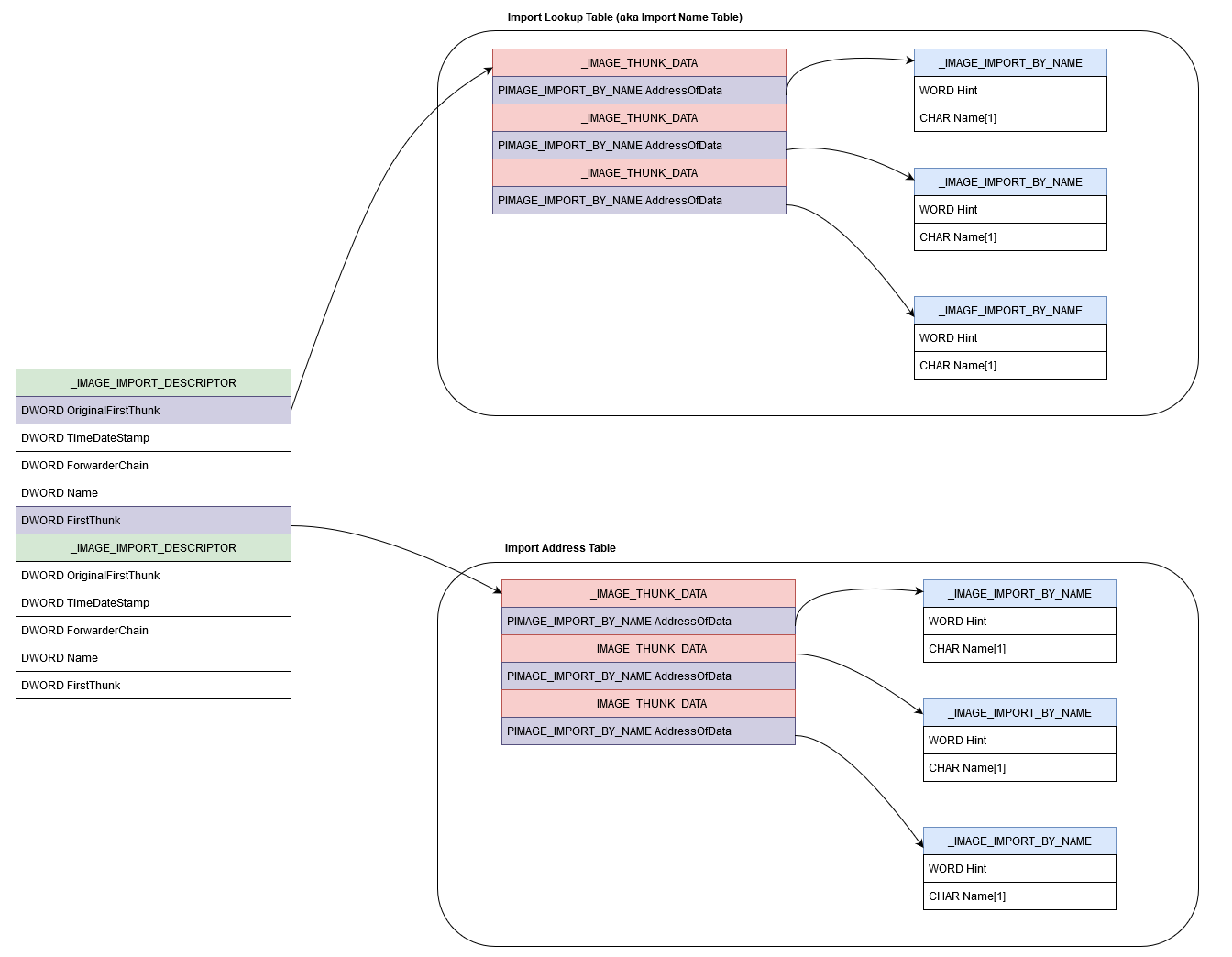
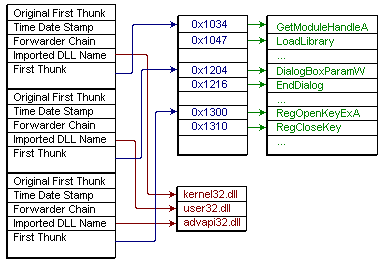
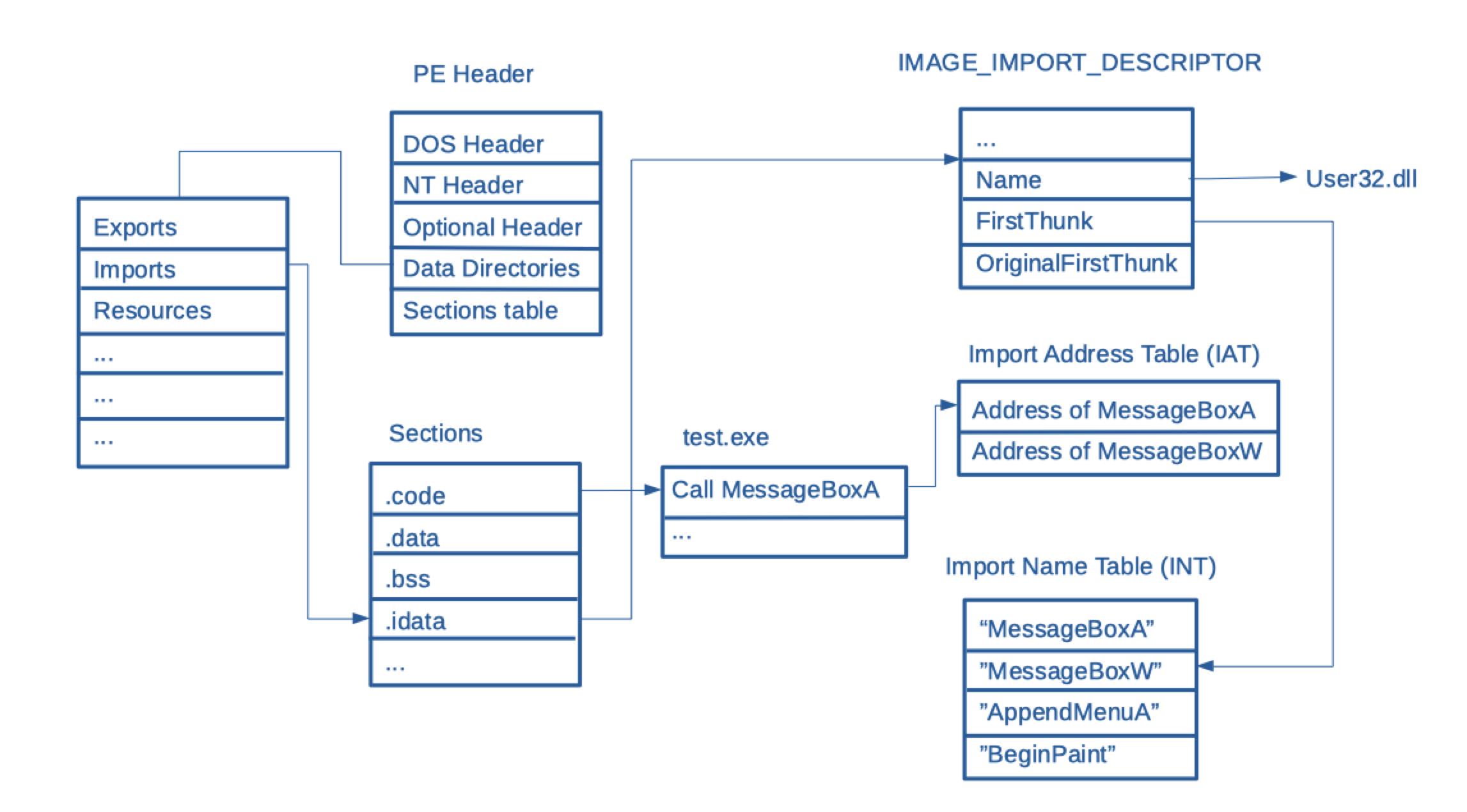
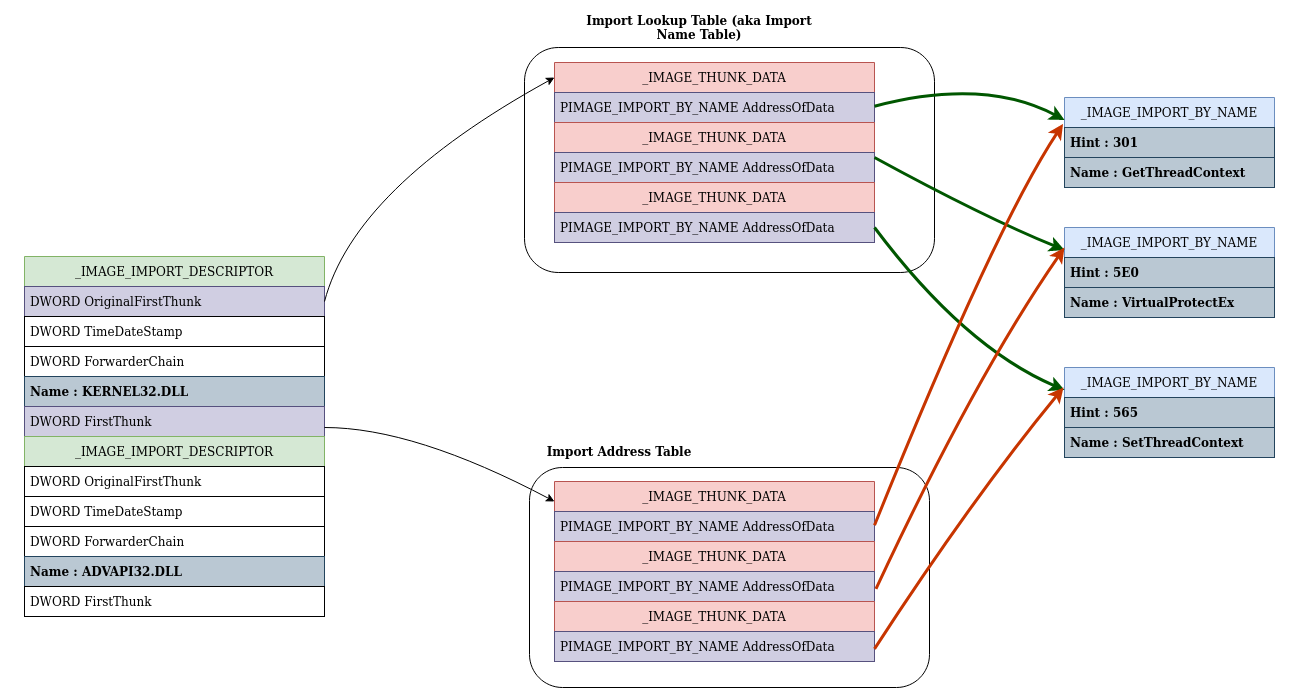
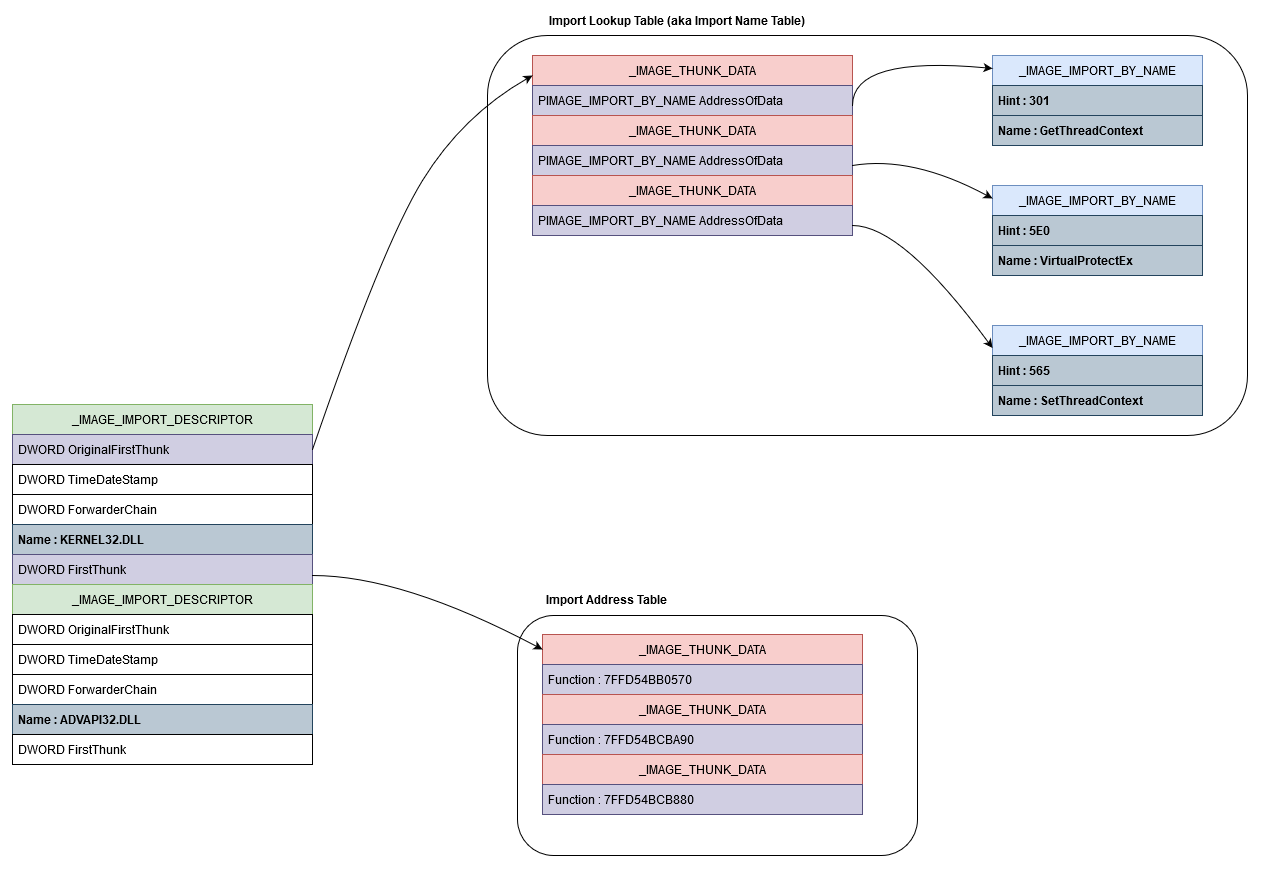
Import hash (IMPHASH) is generated based on the Import Address Table... | Download Scientific Diagram

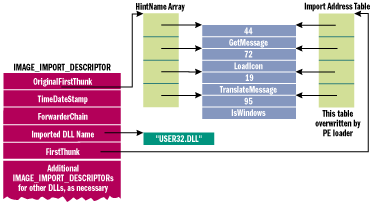
Reverse Engineering and More on Twitter: "RE tip of the day: IAT (import address table) hooking is another form of API hooking where the attackers modify the import table's addresses so that





.gif)