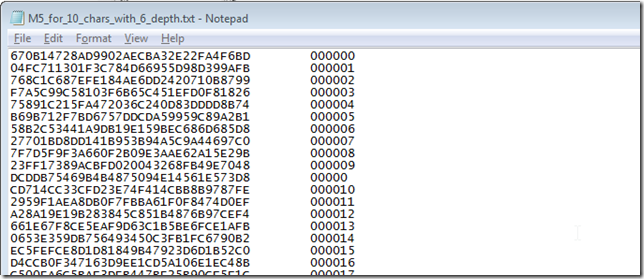
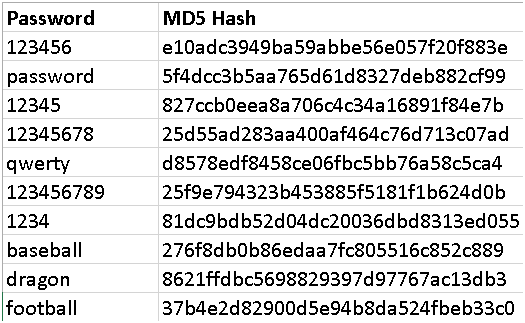
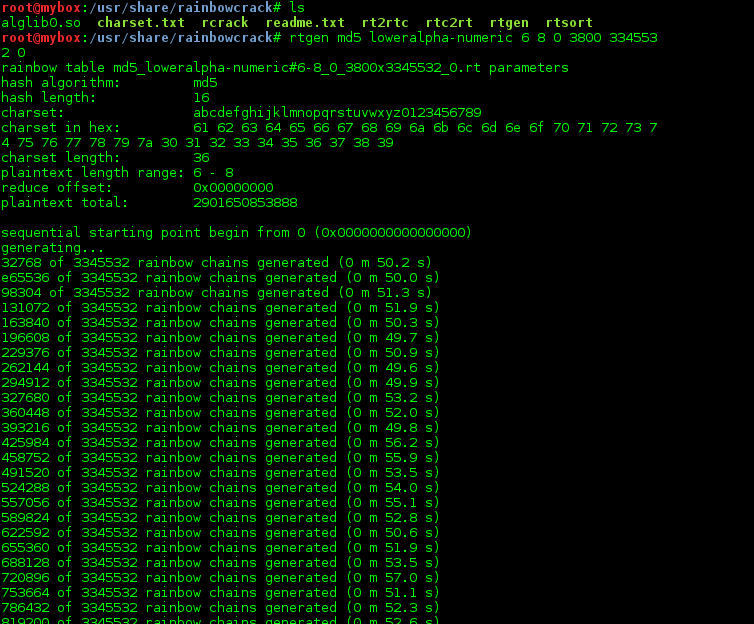
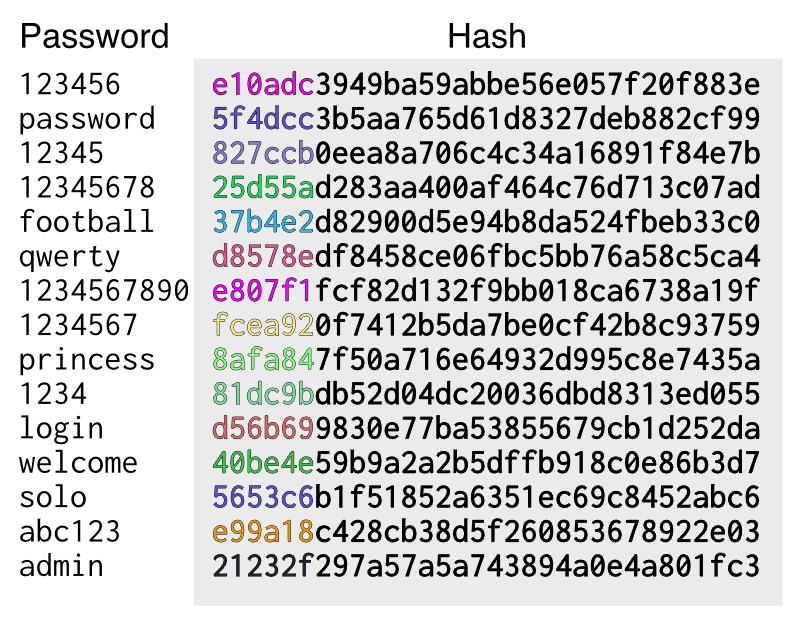
GitHub - alcidesmig/md5-rainbow-table-gen-opencl: MD5 Rainbow table generator using gpu/cpu/fpga (OpenCL) for a pre-defined or generated wordlist.
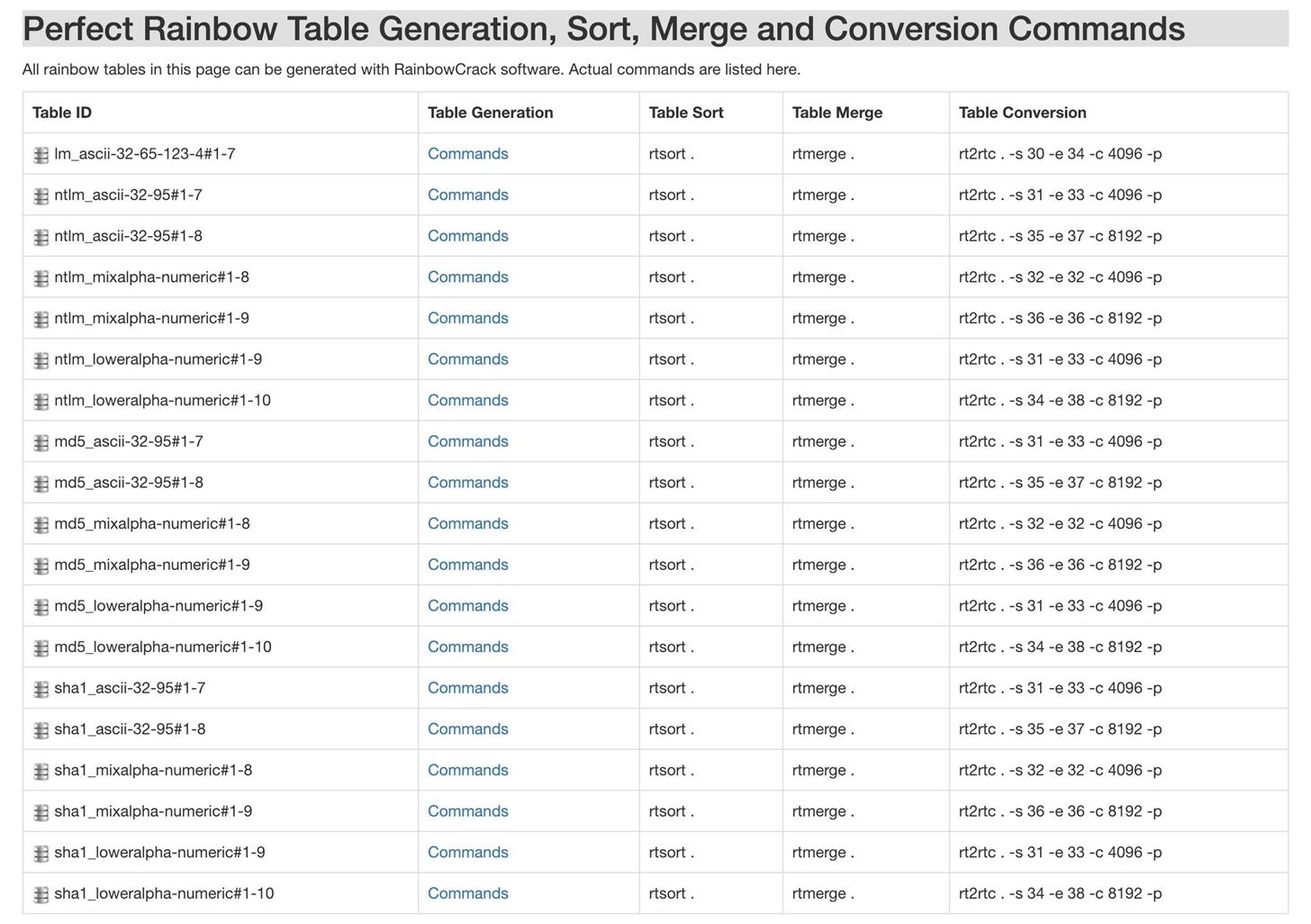
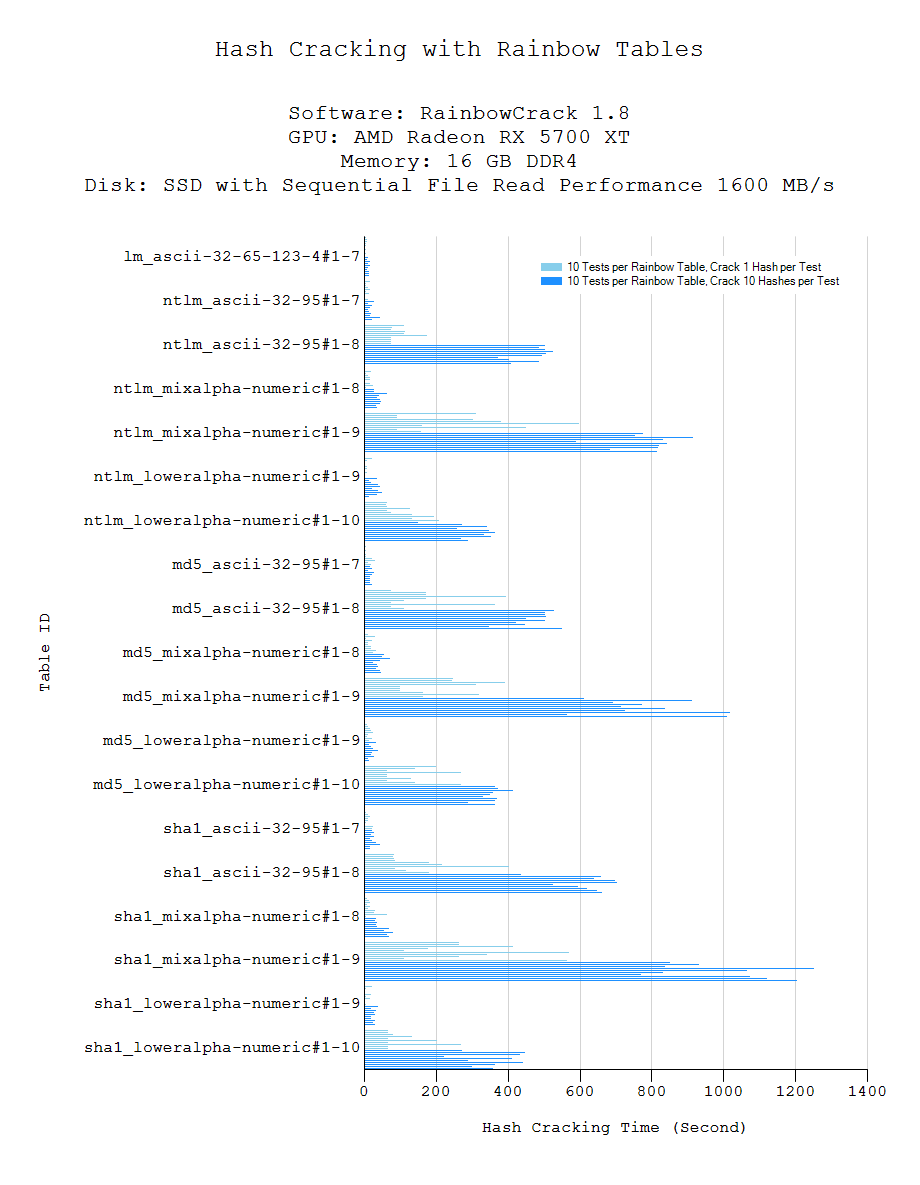
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo
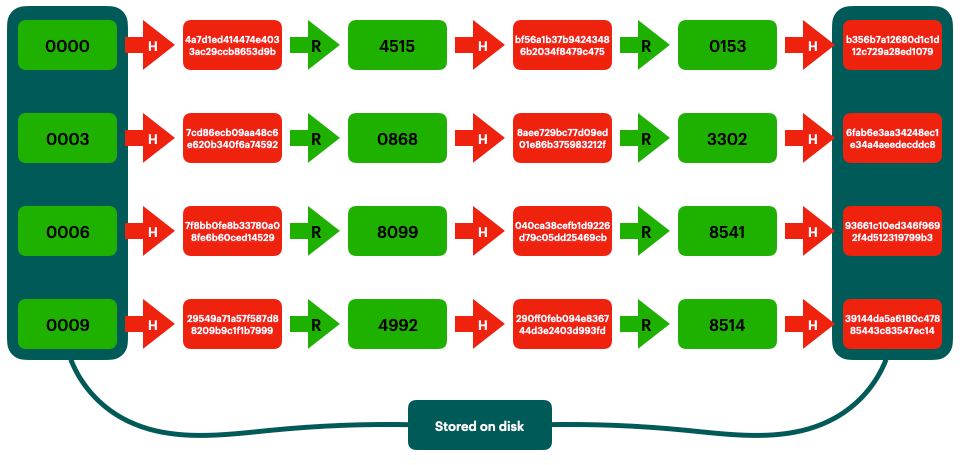
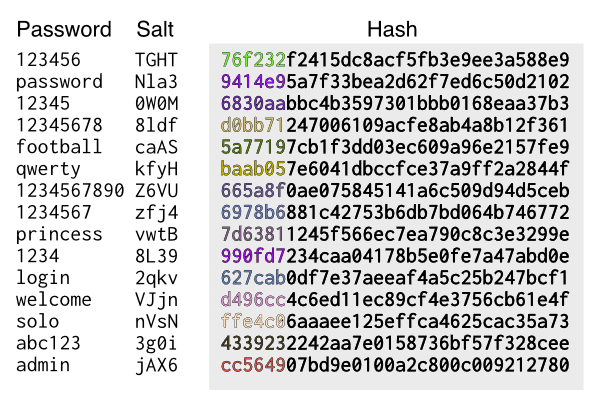
Rainbow Tables (probably) aren't what you think — Part 1: Precomputed Hash Chains | by Ryan Sheasby | Medium
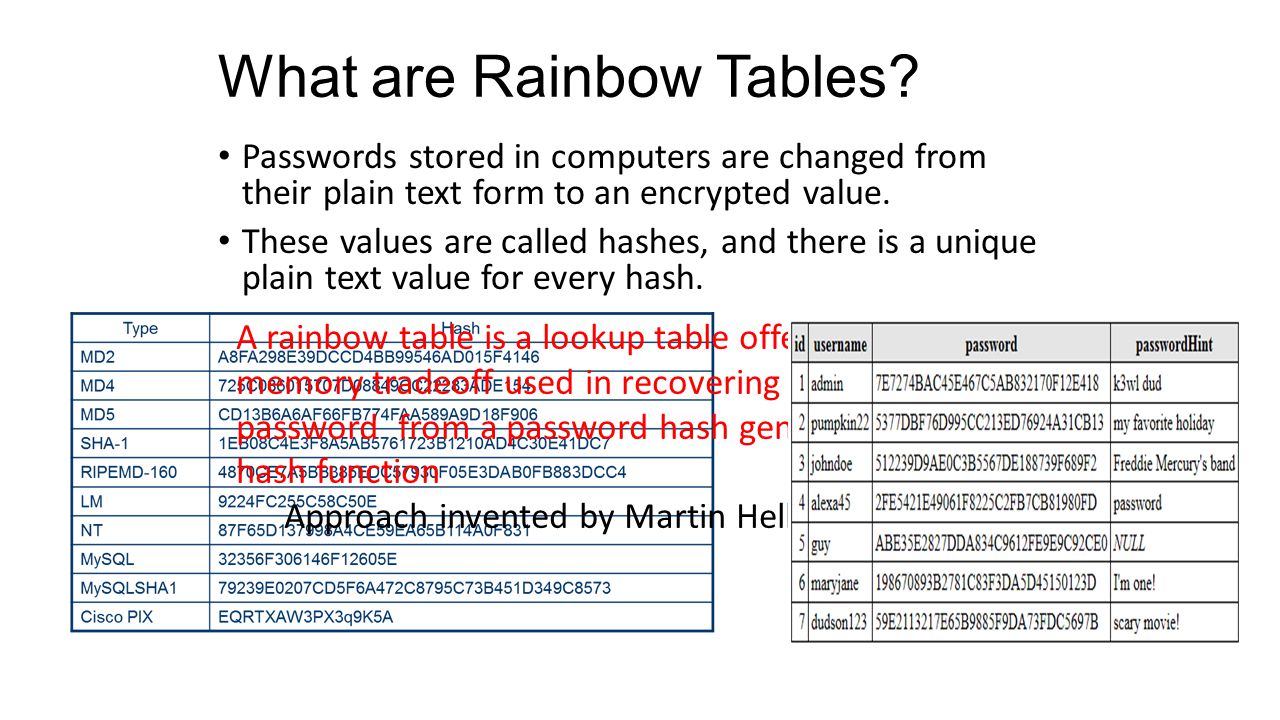
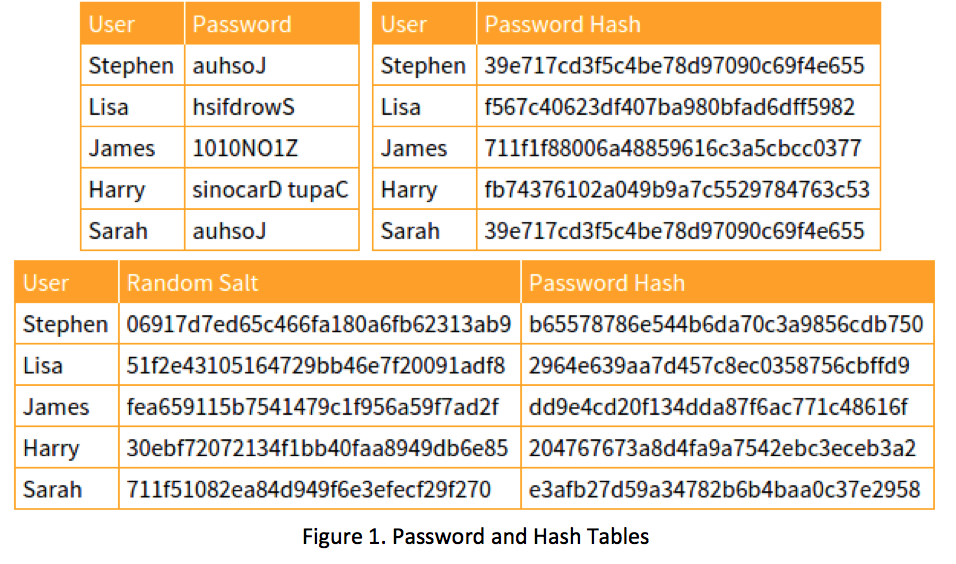
What are Rainbow Tables? Passwords stored in computers are changed from their plain text form to an encrypted value. These values are called hashes, and. - ppt download
GitHub - AurelioDeRosa/Audero-MD5-Rainbow-Table: Audero MD5 Rainbow Table is a precomputed table, made of 11.110.097 entries, for reversing strings encrypted using the MD5 hash function.

I͛P͛h͛o͛n͛e͛G͛a͛l͛a͛x͛y͛M͛D͛ 11K͛ 🏴☠️ on Twitter: "Rainbow table attack #attack #attacks #cyber #cybersecurity #cyberattack #hash #table #hashing #hac #hacks #hack #hacker #hacked #hacker #hackers #hacking #ddos #awareness #aware #safe #security ...