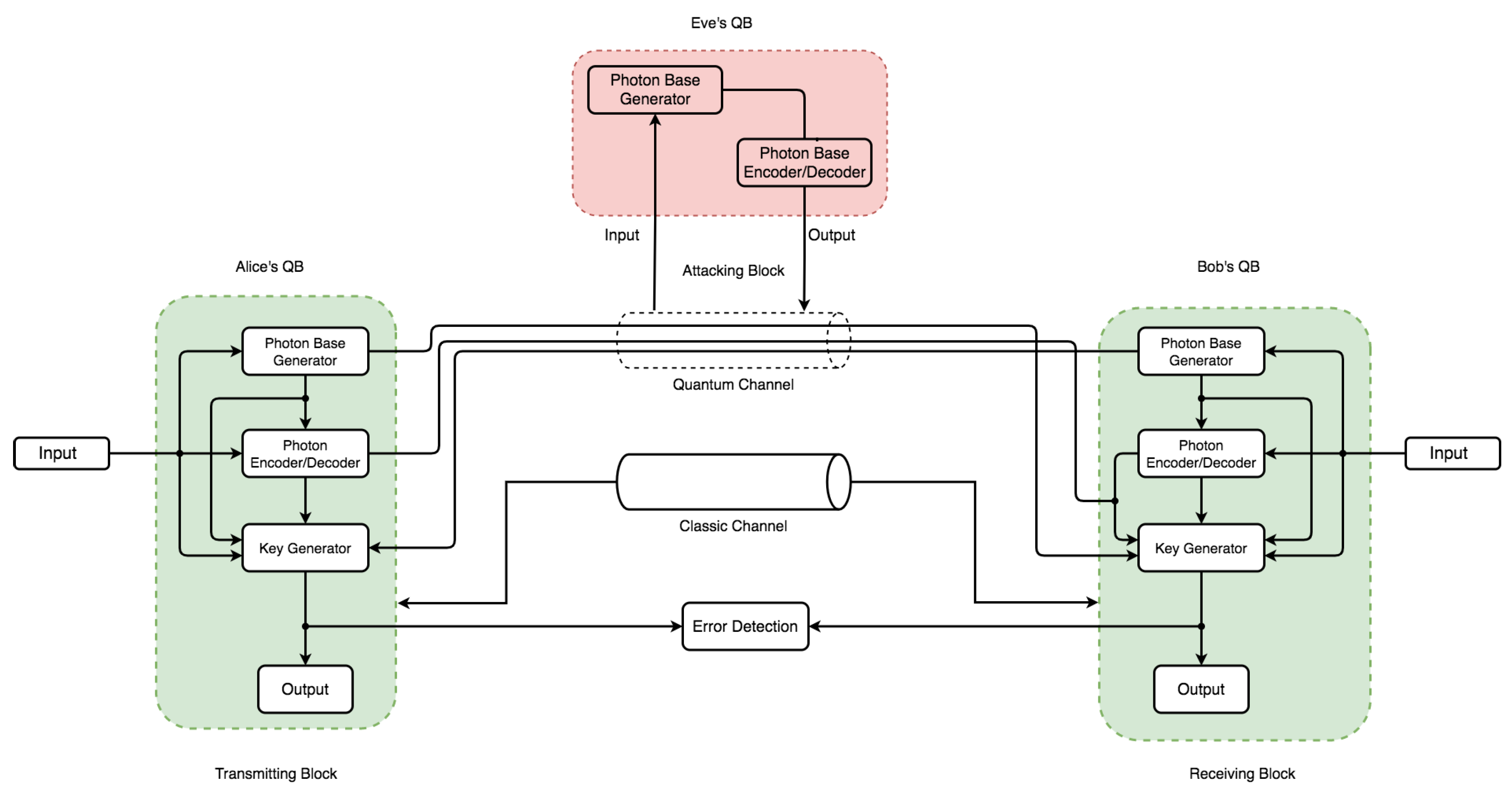
Sensors | Free Full-Text | Quantum Key Distribution: Modeling and Simulation through BB84 Protocol Using Python3 | HTML

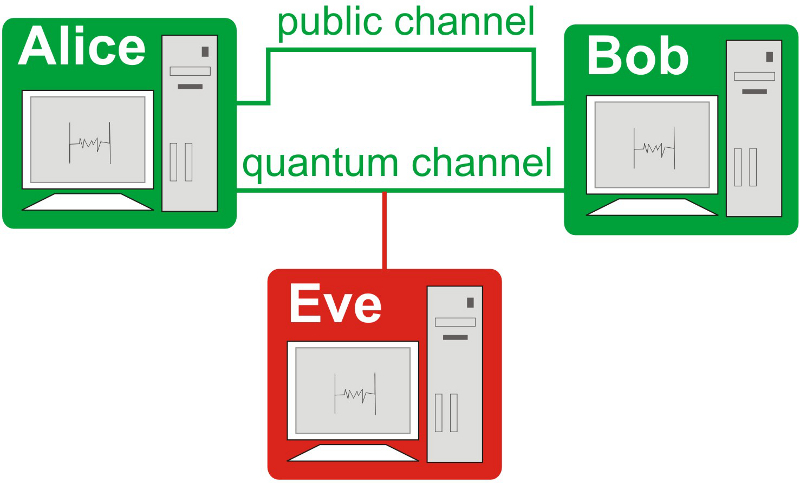
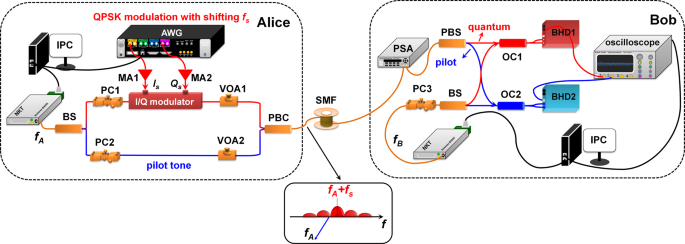
IBM quantum key transmission apparatus. (RNG = random number generator) | Download Scientific Diagram

IBM quantum key transmission apparatus. (RNG = random number generator) | Download Scientific Diagram
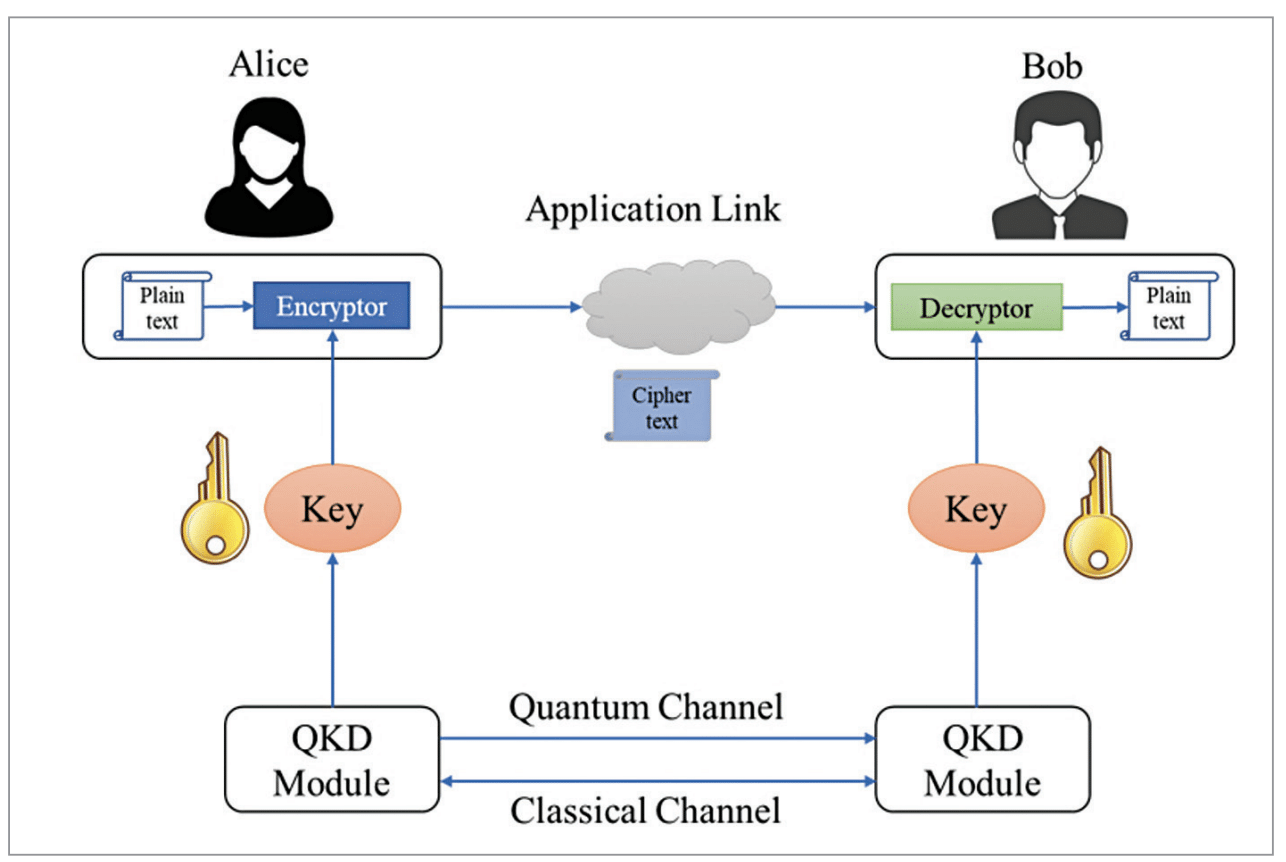
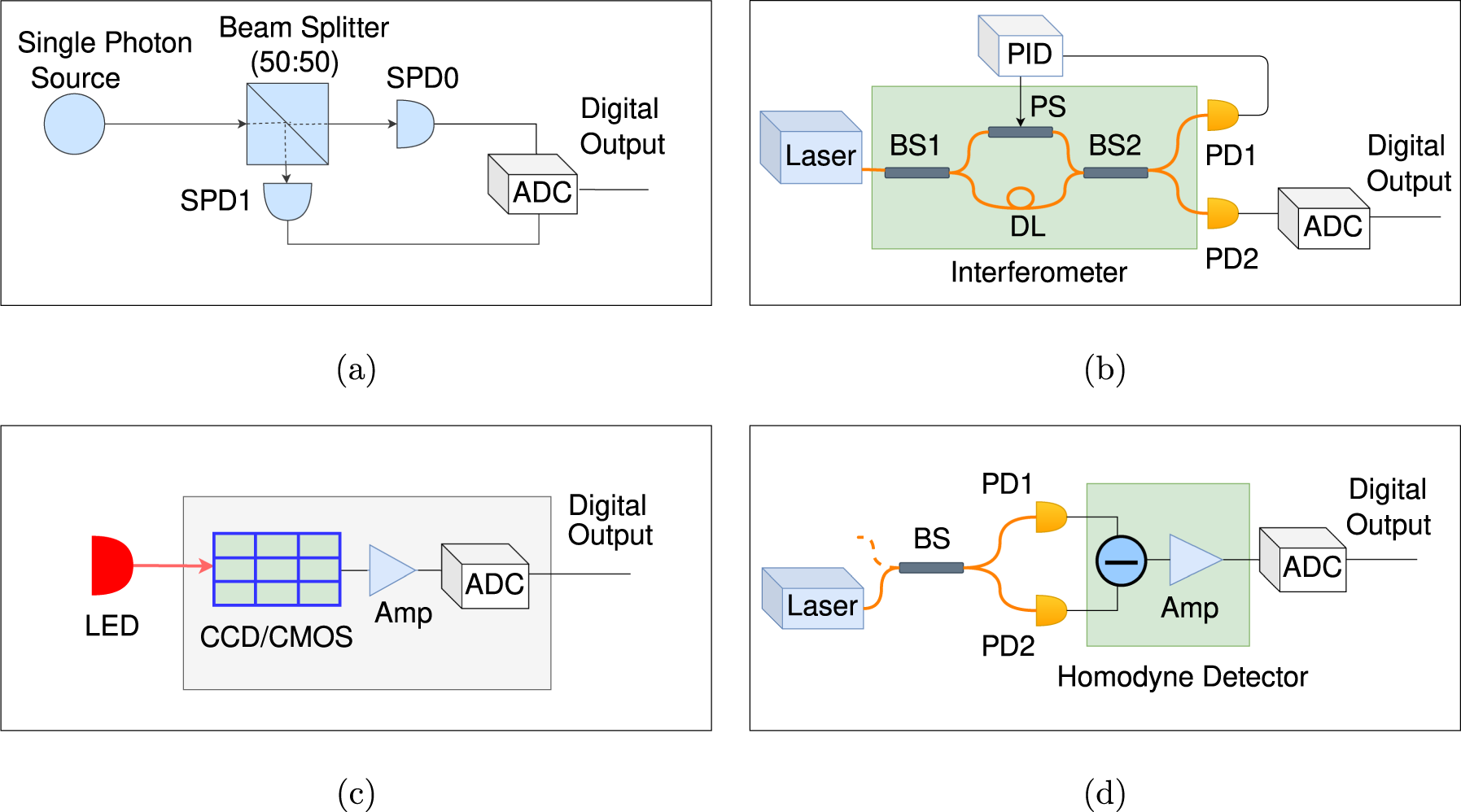







![pib] Quantum Key Distribution - Civilsdaily pib] Quantum Key Distribution - Civilsdaily](https://d18x2uyjeekruj.cloudfront.net/wp-content/uploads/2022/02/qkd.jpg)