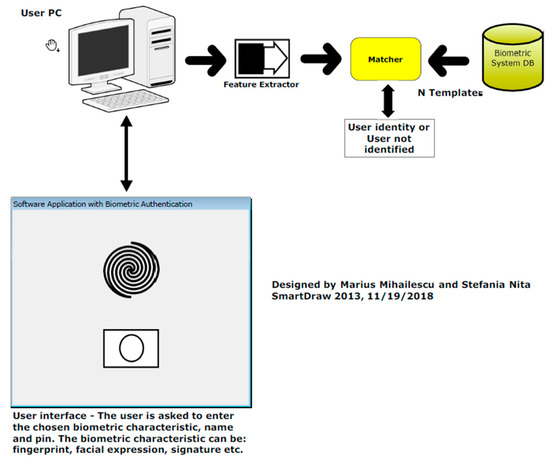
Cryptography | Free Full-Text | Security and Cryptographic Challenges for Authentication Based on Biometrics Data | HTML
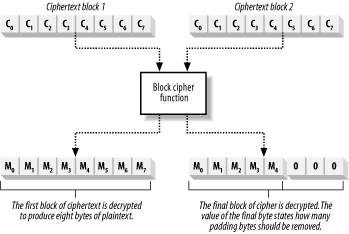
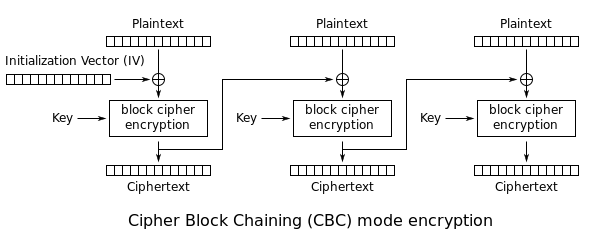
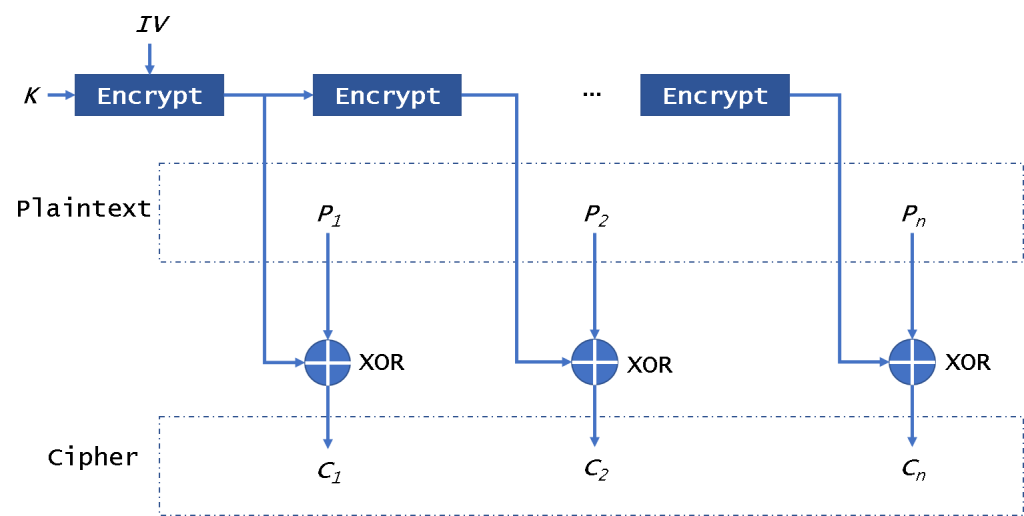
14.2 Symmetric Encryption Explained :: Chapter 14. Symmetric Encryption :: Part III: .NET Cryptography :: .NET Programming security :: Programming :: eTutorials.org
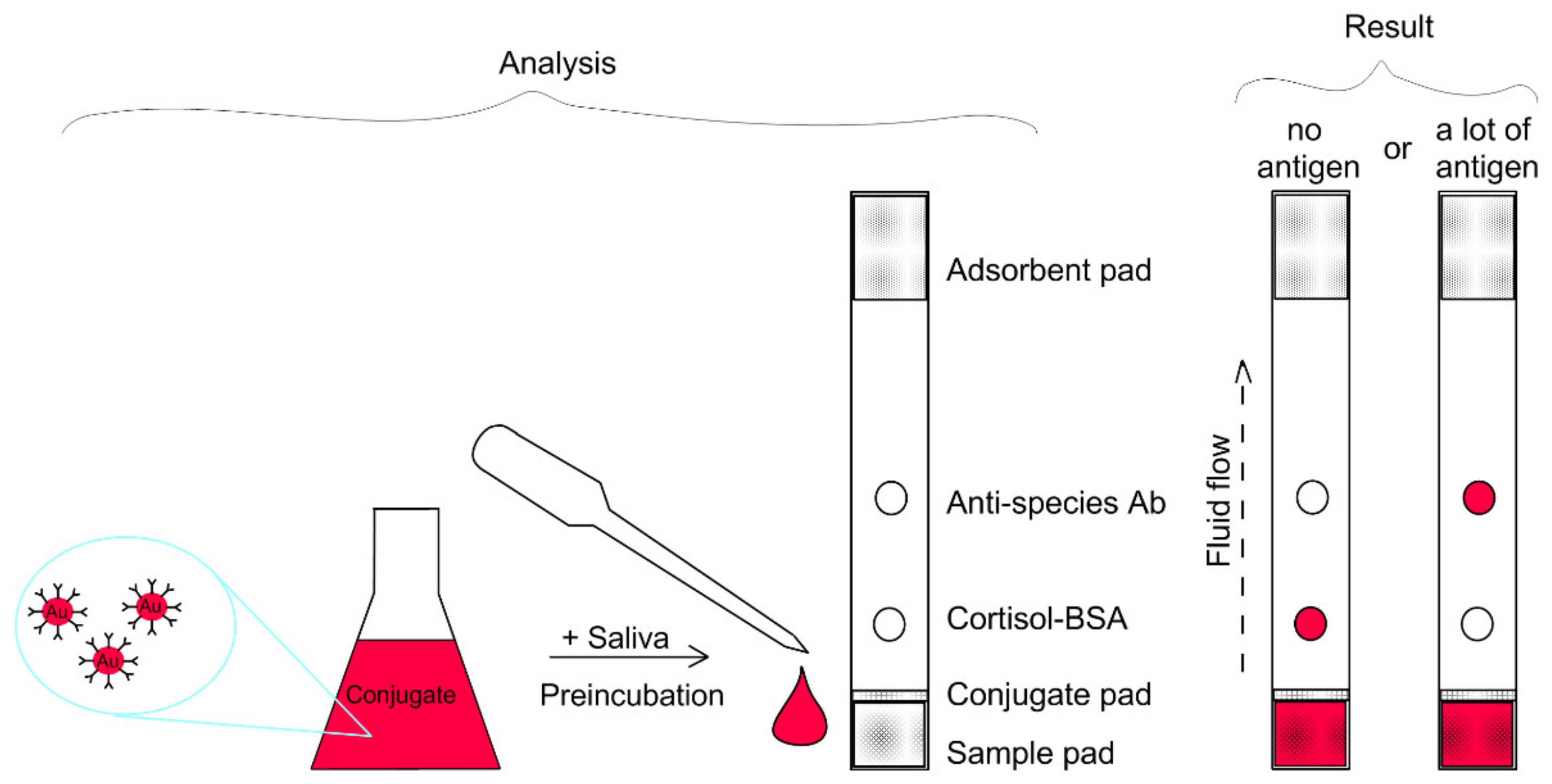
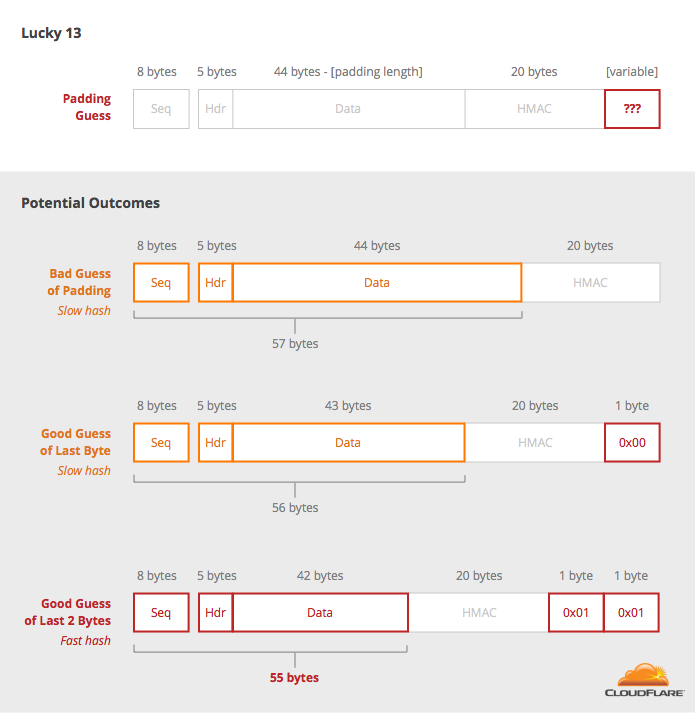
Biosensors | Free Full-Text | Development of a Prototype Lateral Flow Immunoassay of Cortisol in Saliva for Daily Monitoring of Stress | HTML

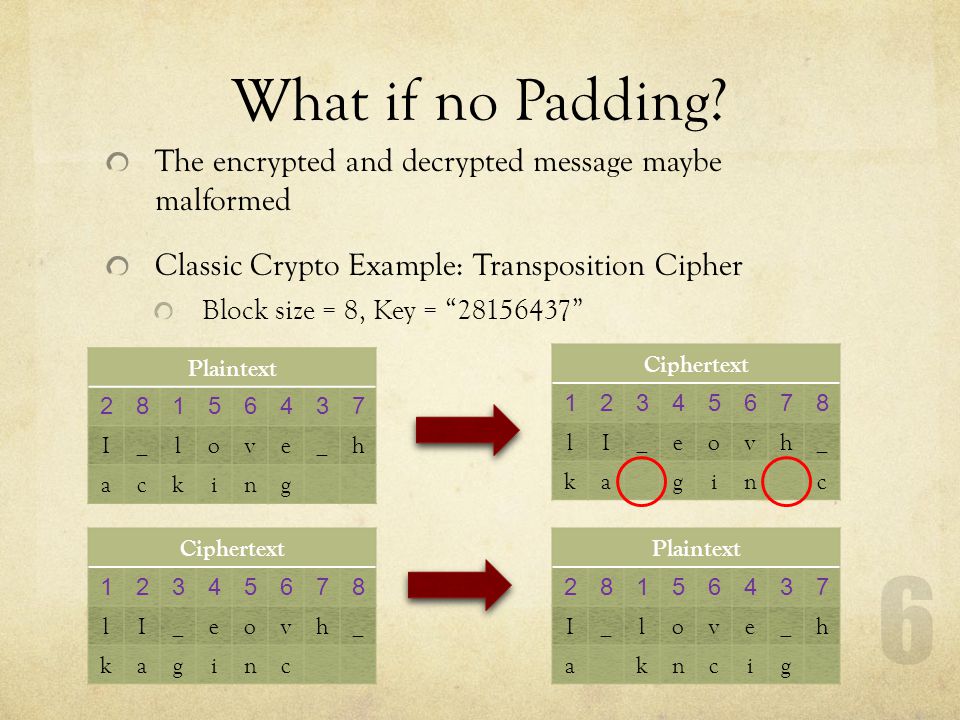
Information | Free Full-Text | Local Multi-Head Channel Self-Attention for Facial Expression Recognition | HTML