Here Are the 9 Best Pavilions at the 2022 Venice Biennale, From Some Super Creepy Centaurs to a Vision of Cybernetic Beauty

NATO - News: NATO will defend itself (Article by NATO Secretary General Jens Stoltenberg published in Prospect), 27-Aug.-2019

Attacking Artificial Intelligence: AI's Security Vulnerability and What Policymakers Can Do About It | Belfer Center for Science and International Affairs
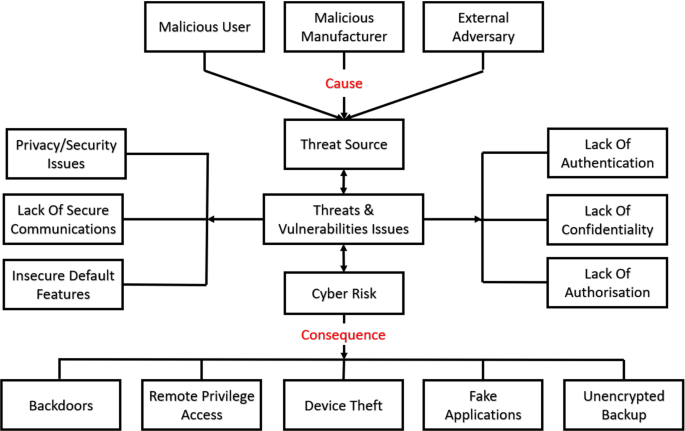
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink